378
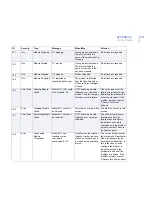
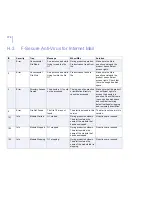
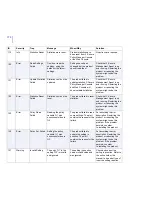
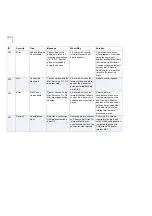
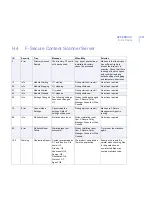
181
Warning
Quarantine
Directory Near
Max Capacity
The volume containing
the Quarantine
Directory is near its
maximum capacity.
Space available on the
disk is %1 megabytes.
Delete some files to
free space.
The disk is getting full.
Free some disk space or
consider moving the
quarantine folder to another
disk.
182
Warning
Quarantine Size
Threshold
The size of the
Quarantine Directory
has reached its
threshold. Current size
of the Quarantine
Directory is %1
megabytes. Space
available on the disk is
%2 megabytes.
Quarantine directory size
threshold has been
reached and/or disk is
getting full.
Free some disk space, or
consider moving the
quarantine folder to another
disk, or increase the
threshold value if there is
enough disk space.
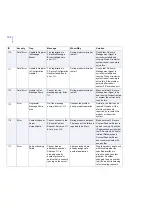
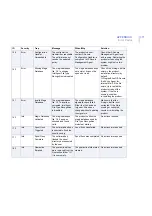
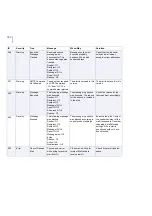
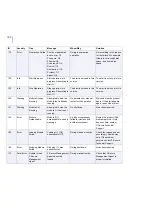
183
Warning
Quarantined
Items Threshold
The total number of
quarantined items has
reached its threshold.
The current number of
items in the quarantine
database is %1.
The total number of
quarantined items has
reached its threshold.
Increase the threshold
value, or adjust the
quarantine retention and
cleanup settings so that old
quarantined items are
removed more often. If
necessary, delete old
quarantined items
manually.
190
Info
Old Mail Logs
Removed
Old mail logs were
removed from the log
directory '%1'.
The product automatically
removes old files from the
log directory.
No actions are required.
191
Info
Mail Log Emptied The current mail log file
'%1' was emptied.
The product empties the
mail log file.
No actions are required.
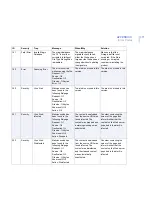
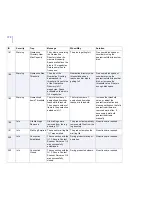
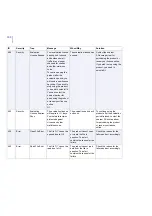
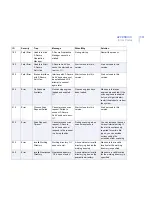
200
Info
Connection
Established
The connection with the
%1 F-Secure Content
Scanner Server on %2
was successfully
established.
During product startup or
operation.
No actions are required.
205
Info
Connection
Closed
The connection with the
%1 F-Secure Content
Scanner Server on %2
was successfully
closed.
During product shutdown.
No actions are required.
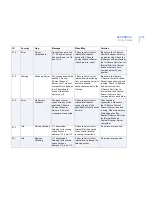
ID
Severity
Trap
Message
When/Why
Solution
Summary of Contents for INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61...
Page 1: ...F Secure Internet Gatekeeper Windows 2000 2003 Server Administrator s Guide...
Page 10: ...10 ABOUT THIS GUIDE How This Guide is Organized 11 Conventions Used in F Secure Guides 13...
Page 26: ...26 2 DEPLOYMENT Overview 27 Deployment Scenarios 29...
Page 58: ...58 Step 10 Enter the IP address of the F Secure Policy Manager Server Click Next to continue...
Page 261: ...CHAPTER10 261 Quarantine Management Figure 10 1 Quarantine Query page...
Page 296: ...296 A APPENDIX Warning Messages HTTP Warning Messages 297 SMTP Warning Messages 298...
Page 304: ...304 C APPENDIX Access Log Variables List of Access Log Variables 305...
Page 309: ...309 D APPENDIX Mail Log Variables List of Mail Log Variables 310...
Page 360: ...360 G APPENDIX Services and Processes List of Services and Processes 361...
Page 414: ...414...