CHAPTER 3
69
Installation
3.4
After the Installation
This section describes what you have to do after the installation to take
F-Secure Internet Gatekeeper into use.
3.4.1
Importing Product MIB files to F-Secure Policy Manager
Console
If you are using the product in centrally managed mode, there are cases
when the F-Secure Internet Gatekeeper MIB JAR file cannot be uploaded
to F-Secure Policy Manager Server during the installation. In these cases
you will have to import the MIB files to F-Secure Policy Manager. You will
have to import the MIB files if:
F-Secure Internet Gatekeeper is located in a different network
segment than F-Secure Policy Manager, and there is a firewall
between them blocking access to Policy Manager’s
administrative port (8080).
F-Secure Policy Manager Server has been configured so that
administrative connections from anywhere else than the localhost
are blocked. This is the default F-Secure Policy Manager Server
configuration.
The recommended way is to import the MIBs via F-Secure Policy
Manager Console’s
Tools
menu. The F-Secure Internet Gatekeeper MIB
JAR file is located on the F-Secure CD in the
\software\fsig\mibs\
directory. You can import the MIBs as follows:
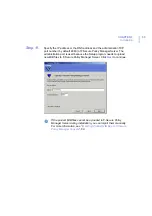
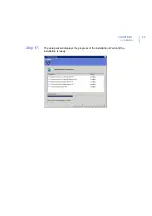
1.
Open the
Tools
menu and select the
Installation packages...
option.
2.
Click I
mport...
.
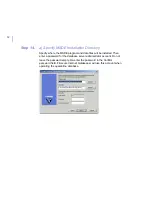
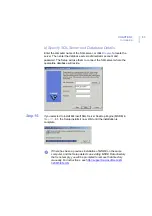
3.
When the Import Installation Packages dialog opens, browse to
locate the
fsigk661mib.jar
file. Then click
Open
.
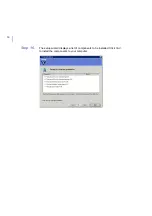
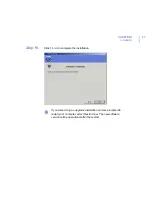
4.
After importing the new MIB files, restart F-Secure Policy Manager
Console.
Another possibility for importing the product MIBs is to run the
imptmib.exe
utility from the F-Secure CD.
Summary of Contents for INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61...
Page 1: ...F Secure Internet Gatekeeper Windows 2000 2003 Server Administrator s Guide...
Page 10: ...10 ABOUT THIS GUIDE How This Guide is Organized 11 Conventions Used in F Secure Guides 13...
Page 26: ...26 2 DEPLOYMENT Overview 27 Deployment Scenarios 29...
Page 58: ...58 Step 10 Enter the IP address of the F Secure Policy Manager Server Click Next to continue...
Page 261: ...CHAPTER10 261 Quarantine Management Figure 10 1 Quarantine Query page...
Page 296: ...296 A APPENDIX Warning Messages HTTP Warning Messages 297 SMTP Warning Messages 298...
Page 304: ...304 C APPENDIX Access Log Variables List of Access Log Variables 305...
Page 309: ...309 D APPENDIX Mail Log Variables List of Mail Log Variables 310...
Page 360: ...360 G APPENDIX Services and Processes List of Services and Processes 361...
Page 414: ...414...