310
D.1
List of Mail Log Variables
You can use the following macros to specify what kind of information is
collected from different events in the F-Secure Anti-Virus for Internet Mail
mail log.
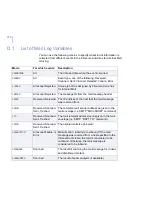
Macro
For which events
Description
$DATETIME
All
The date and time when the event occurred
$EVENT
All
Event type, one of the following:
Received
,
Scanned
,
Sent
,
Trashed
,
Rejected
,
Failure
,
Error
.
$JOBID
All except Rejected
Unique job ID as assigned by F-Secure Anti-Virus
for Internet Mail.
$MSGID
All except Rejected
The message ID from the mail message header.
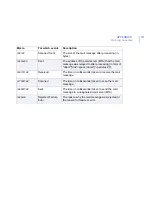
$HOST
Received, Rejected
The IP address of the host that the mail message
was received from.
$FROM
Received, Scanned,
Sent, Trashed
The complete mail sender address as given in the
mail envelope (i.e. SMTP "MAIL FROM" command).
$TO
Received, Scanned,
Sent, Trashed
The mail recipient address(es) as given in the mail
envelope (i.e. SMTP "RCPT TO" command).
$SIZE
Received, Scanned,
Sent, Trashed
The original mail size (in bytes).
$DIRECTION
All except Failure or
Error
Mail direction: inbound or outbound. If the mail
message was received from a host specified in the
Intranet Hosts table, the mail is considered to be
outbound. Otherwise, the mail message is
considered to be inbound.
$SCANRES
Scanned
The result of scanning the mail message for viruses
and disallowed content.
$SPAMCHECK
Scanned
The result of spam analysis (if available).
Summary of Contents for INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61...
Page 1: ...F Secure Internet Gatekeeper Windows 2000 2003 Server Administrator s Guide...
Page 10: ...10 ABOUT THIS GUIDE How This Guide is Organized 11 Conventions Used in F Secure Guides 13...
Page 26: ...26 2 DEPLOYMENT Overview 27 Deployment Scenarios 29...
Page 58: ...58 Step 10 Enter the IP address of the F Secure Policy Manager Server Click Next to continue...
Page 261: ...CHAPTER10 261 Quarantine Management Figure 10 1 Quarantine Query page...
Page 296: ...296 A APPENDIX Warning Messages HTTP Warning Messages 297 SMTP Warning Messages 298...
Page 304: ...304 C APPENDIX Access Log Variables List of Access Log Variables 305...
Page 309: ...309 D APPENDIX Mail Log Variables List of Mail Log Variables 310...
Page 360: ...360 G APPENDIX Services and Processes List of Services and Processes 361...
Page 414: ...414...