APPENDIX H
391
Error Codes
H.4
F-Secure Content Scanner Server
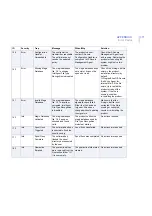
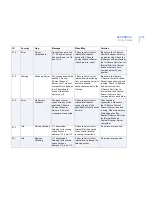
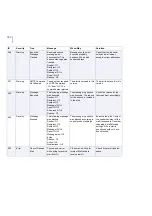
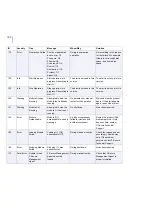
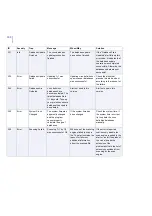
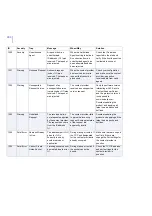
ID
Severity
Trap
Message
When/Why
Solution
3
Error
Directory Access
Denied
The directory %1 could
not be accessed.
Log, spool, quarantine or
installation directory
cannot be accessed
Make sure that the product
has sufficient rights to
access the directory in
question. Check that there
is enough free disk space
and consider restoring
default settings for logging
and temporary directories.
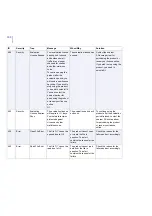
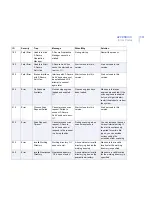
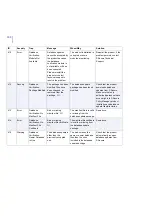
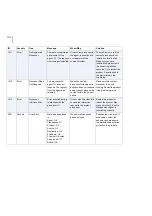
10
Info
Module Starting
%1 starting...
During startup or restart.
No actions required.
20
Info
Module Stopping
%1 stopping...
During shutdown.
No actions required.
30
Info
Module Started
%1started
During startup or restart.
No actions required.
40
Info
Module Stopped
%1 stopped
During shutdown.
No actions required.
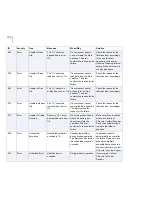
50
Info
Settings Changed
The following settings
have been changed:
%1
Product settings changed
from F-Secure Policy
Manager Console or Web
Console.
No actions required.
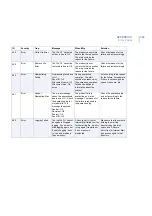
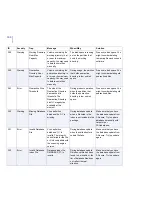
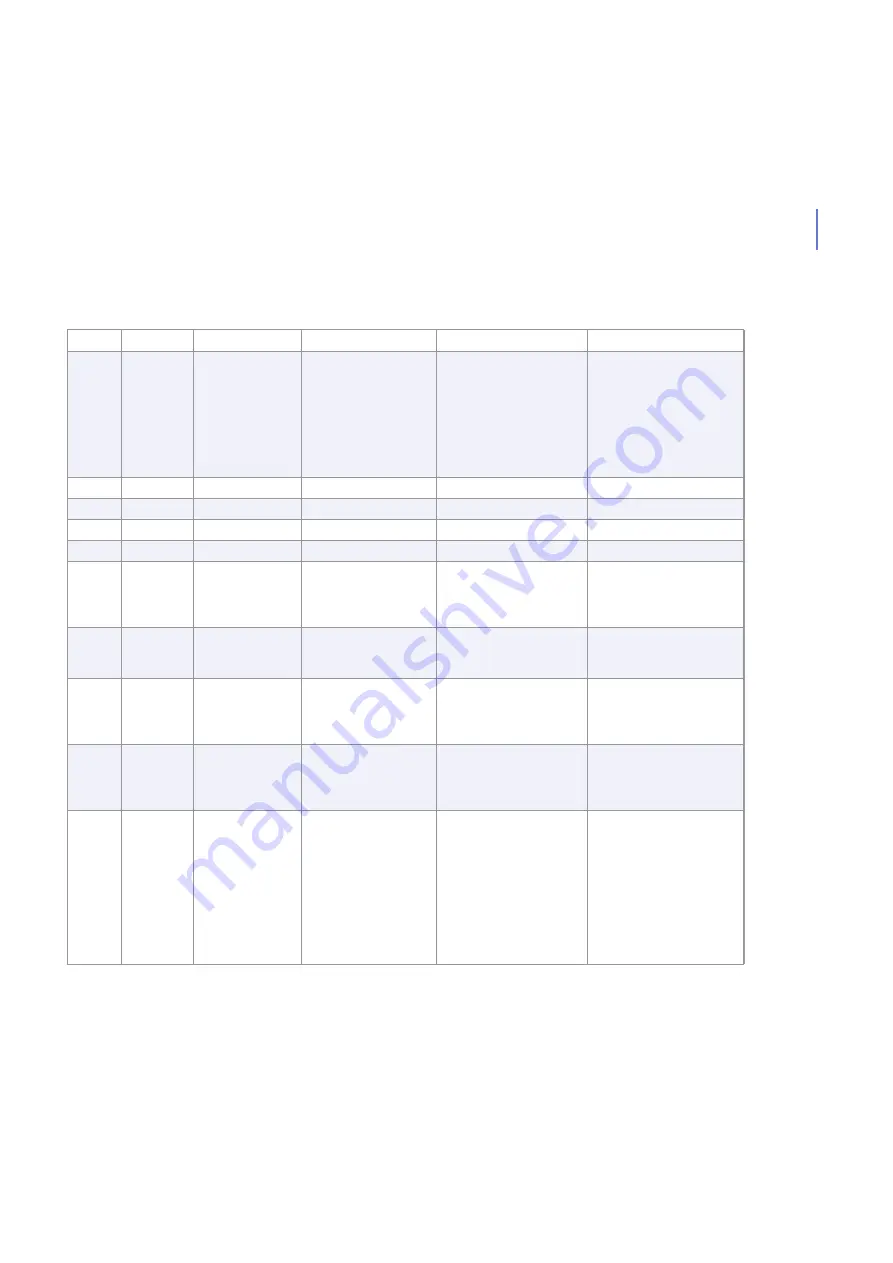
70
Error
Cannot Read
Settings
Cannot read the
settings. Default
settings will be used.
During startup or restart.
Make sure F-Secure
Management Agent is
running.
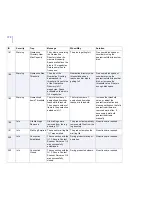
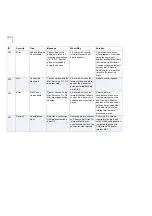
80
Info
Statistics Reset
Statistics were reset.
Product statistics reset
from F-Secure Policy
Manager Console or Web
Console.
No actions required.
90
Error
Statistics Reset
Failed
Statistics reset not
successful.
Product statistics reset
from F-Secure Policy
Manager Console or Web
Console.
Try to reset the statistics
again.
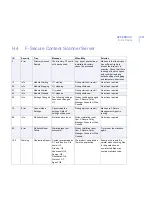
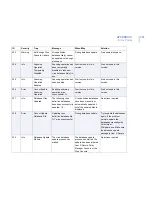
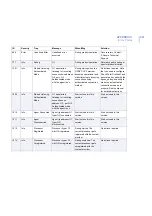
100
Warning
Quarantine Report Content quarantined as
%1 and found in: File
name: %2,
File size :%3,
Scan result: %4,
Source: %5,
Destination: %6,
Protocol: %7,
Agent: %8
The product has placed a
file in the quarantine.
Examine the report. Be
careful when checking files
in the quarantine, as
non-infected files may
contain malicious code.
Summary of Contents for INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61...
Page 1: ...F Secure Internet Gatekeeper Windows 2000 2003 Server Administrator s Guide...
Page 10: ...10 ABOUT THIS GUIDE How This Guide is Organized 11 Conventions Used in F Secure Guides 13...
Page 26: ...26 2 DEPLOYMENT Overview 27 Deployment Scenarios 29...
Page 58: ...58 Step 10 Enter the IP address of the F Secure Policy Manager Server Click Next to continue...
Page 261: ...CHAPTER10 261 Quarantine Management Figure 10 1 Quarantine Query page...
Page 296: ...296 A APPENDIX Warning Messages HTTP Warning Messages 297 SMTP Warning Messages 298...
Page 304: ...304 C APPENDIX Access Log Variables List of Access Log Variables 305...
Page 309: ...309 D APPENDIX Mail Log Variables List of Mail Log Variables 310...
Page 360: ...360 G APPENDIX Services and Processes List of Services and Processes 361...
Page 414: ...414...