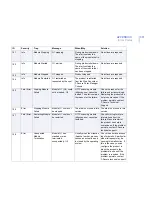
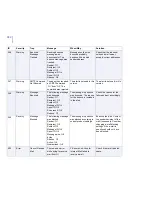
370
130
Info
Settings Changed
The following settings
have been changed:
%1.
Product settings have
been changed from
F-Secure Policy Manager
Console or the Web
Console. The alert
contains the list of settings
that have been changed.
No actions are required.
131
Error
Policy Read
Failed
Reading policy variable
%1 was unsuccessful
due to %2.
The product failed to read
some settings. The alert
contains the reason for the
failure.
Act according to the error
description. Restarting the
product or rebooting the
system might help solve
this problem. If the problem
persists, consider
re-installing the product.
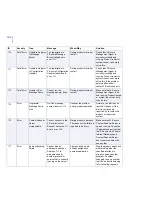
132
Error
Policy Set Failed
Setting policy variable
%1 was unsuccessful
due to %2.
The product failed to
update the setting in
question. The alert
contains the reason for the
failure.
Act according to the error
description. Restarting the
product or rebooting the
system might help solve
this problem. If the problem
persists, consider
re-installing the product.
133
Warning
Invalid Setting
The entry '%1' in the
setting '%2' is invalid
and ignored.
During product startup or
restart.
Check and correct the
setting in question. Refer to
the online help or the
manual to see what type of
input the setting requires.
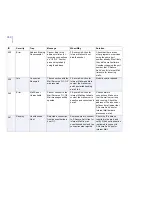
140
Error
Missing Magic
Database
The magic database
file '%1' is missing.
Intelligent File Type
Recognition is disabled.
If the magic database
does not exist or it cannot
be opened or read. Most
likely, the file does not
exist or the httpscan.exe
process does not have
permission to read it.
Check if the ftrmagic.def file
is present in the product
binary directory (by default,
%ProgramFiles%\F-Secure
\Anti-Virus for Internet
Gateways\bin). If the file
exists, try to restart the
product or reboot the
system. If the file is
missing, consider
re-installing the product.
ID
Severity
Trap
Message
When/Why
Solution
Summary of Contents for Internet Gatekeeper
Page 1: ...F Secure Internet Gatekeeper Windows 2000 2003 Server Administrator s Guide ...
Page 10: ...10 ABOUT THIS GUIDE How This Guide is Organized 11 Conventions Used in F Secure Guides 13 ...
Page 26: ...26 2 DEPLOYMENT Overview 27 Deployment Scenarios 29 ...
Page 58: ...58 Step 10 Enter the IP address of the F Secure Policy Manager Server Click Next to continue ...
Page 261: ...CHAPTER10 261 Quarantine Management Figure 10 1 Quarantine Query page ...
Page 296: ...296 A APPENDIX Warning Messages HTTP Warning Messages 297 SMTP Warning Messages 298 ...
Page 304: ...304 C APPENDIX Access Log Variables List of Access Log Variables 305 ...
Page 309: ...309 D APPENDIX Mail Log Variables List of Mail Log Variables 310 ...
Page 360: ...360 G APPENDIX Services and Processes List of Services and Processes 361 ...
Page 414: ...414 ...