7 - 18
ForeRunner
ATM Switch Network Configuration Manual
Signalling
7.4 Allowable Combination of Traffic Parameters
7.4.1 PNNI 1.0/UNI 4.0
The following information applies to both signalled connections and to PNNI SPVCs.
7.4.1.1 Service Categories
The ATM service categories assigned to connections in PNNI 1.0 and UNI 4.0 are defined in
the ATM Traffic Management Specification, Version 4.0 (TM 4.0). For PNNI 1.0 interfaces,
ForeThought 5.2.x supports the service categories defined in TM 4.0 with a few exceptions.
An explicit way of requesting a particular ATM service category is not provided in PNNI 1.0
and UNI 4.0 signalling. Instead, it must be derived from three pieces of information in the
SETUP message.
•
the broadband bearer class in octet 5 of the broadband bearer capability (BBC)
information element
•
the absence or presence of the ATM transfer capability (ATC) octet (octet 5a) in the
BBC information element
•
the value of the ATC, if present, and the absence or presence of the best effort indi-
cator in octet 18 of the ATM Traffic Descriptor information element
Derivation of a service category from the above information is specified in Section A9.2
(Determination of ATM service Category) of the ATM User-Network Interface (UNI) Signal-
ling Specification, Version 4.0 (UNI 4.0). However, ForeThought 5.2.x does not support the fol-
lowing from Table A9-1 of this specification:
•
The Transparent VP-Service in the BBC information element is not supported.
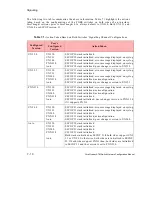
7.4.1.2 Allowable Combination of Traffic Parameters
The parameters specified in the BBC information element, the ATM traffic descriptor informa-
tion element, the Extended QoS parameter information element, the End-to-End transit delay
information element, and the QoS parameter information element of the SETUP message
should be consistent.
Table A9-2 of UNI 4.0 shows the allowable combinations. The following exceptions apply to
ForeThought 5.2.x:
•
In the Extended QoS parameters information element, for forward and backward
Cell Loss Ratio (CLR), ForeThought 5.2.x does not distinguish between the (CLP=0)
and CLP (0+1) traffic streams.
Summary of Contents for forerunner series
Page 6: ......
Page 16: ...TOC 10 ForeRunner ATM Switch Network Configuration Manual Table of Contents ...
Page 20: ...LOF 4 ForeRunner ATM Switch Network Configuration Manual List of Figures ...
Page 22: ...LOT 2 ForeRunner ATM Switch Network Configuration Manual List of Tables ...
Page 30: ...viii ForeRunner ATM Switch Network Configuration Manual Preface ...
Page 144: ...3 58 ForeRunner ATM Switch Network Configuration Manual Configuring an Emulated LAN ...
Page 180: ...6 12 ForeRunner ATM Switch Network Configuration Manual ATM Forum PNNI ...
Page 220: ...9 6 ForeRunner ATM Switch Network Configuration Manual Configuring Timing ...
Page 300: ...D 24 ForeRunner ATM Switch Network Configuration Manual Configuring FramePlus Modules ...
Page 308: ...Acronyms 8 ForeRunner ATM Switch Network Configuration Manual Acronyms ...
Page 346: ...Glossary 38 ForeRunner ATM Switch Network Configuration Manual Glossary ...
Page 352: ...Index 6 ForeRunner ATM Switch Network Configuration Manual Index ...