A - 18
ForeRunner
ATM Switch Network Configuration Manual
Configuring SNMP
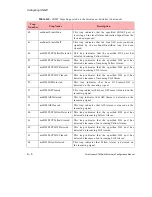
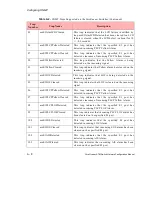
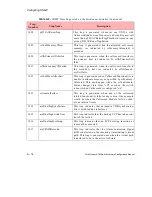
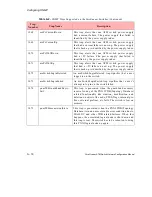
Table A.3 defines the message types and the message requests for Trap 2003.
Table A.3 -
Message Type Encodings for Trap 2003
MessageType
Message Request
0
Configure network module
1
Configure port
2
Send egress Fdl
4
Network module reset
5
Port reset
6
Configure a channel/service
7
Request channel/service configuration
8
Request port configuration
9
Request connection configuration
10
Channel/service reset
17
Configure LEDs
28
Request application revision
29
Create a FUNI service
30
Create a Frame Relay service
31
Request to change service admin status
32
Request to enable/disable service statistics
33
Request to enable/disable network module statistics
34
Request to enable/disable network module admin status
35
Request to enable/disable port admin status
36
Delete a service
37
Create a Frame Relay connection
38
Create a FUNI connection
40
Request to enable/disable connection admin status
41
Request to enable/disable service egress rate enforcement
Summary of Contents for forerunner series
Page 6: ......
Page 16: ...TOC 10 ForeRunner ATM Switch Network Configuration Manual Table of Contents ...
Page 20: ...LOF 4 ForeRunner ATM Switch Network Configuration Manual List of Figures ...
Page 22: ...LOT 2 ForeRunner ATM Switch Network Configuration Manual List of Tables ...
Page 30: ...viii ForeRunner ATM Switch Network Configuration Manual Preface ...
Page 144: ...3 58 ForeRunner ATM Switch Network Configuration Manual Configuring an Emulated LAN ...
Page 180: ...6 12 ForeRunner ATM Switch Network Configuration Manual ATM Forum PNNI ...
Page 220: ...9 6 ForeRunner ATM Switch Network Configuration Manual Configuring Timing ...
Page 300: ...D 24 ForeRunner ATM Switch Network Configuration Manual Configuring FramePlus Modules ...
Page 308: ...Acronyms 8 ForeRunner ATM Switch Network Configuration Manual Acronyms ...
Page 346: ...Glossary 38 ForeRunner ATM Switch Network Configuration Manual Glossary ...
Page 352: ...Index 6 ForeRunner ATM Switch Network Configuration Manual Index ...