86
The FortiGate Cookbook 5.0.
Adding multicast security
policies
Go to
Policy > Policy > Multicast Policy
.
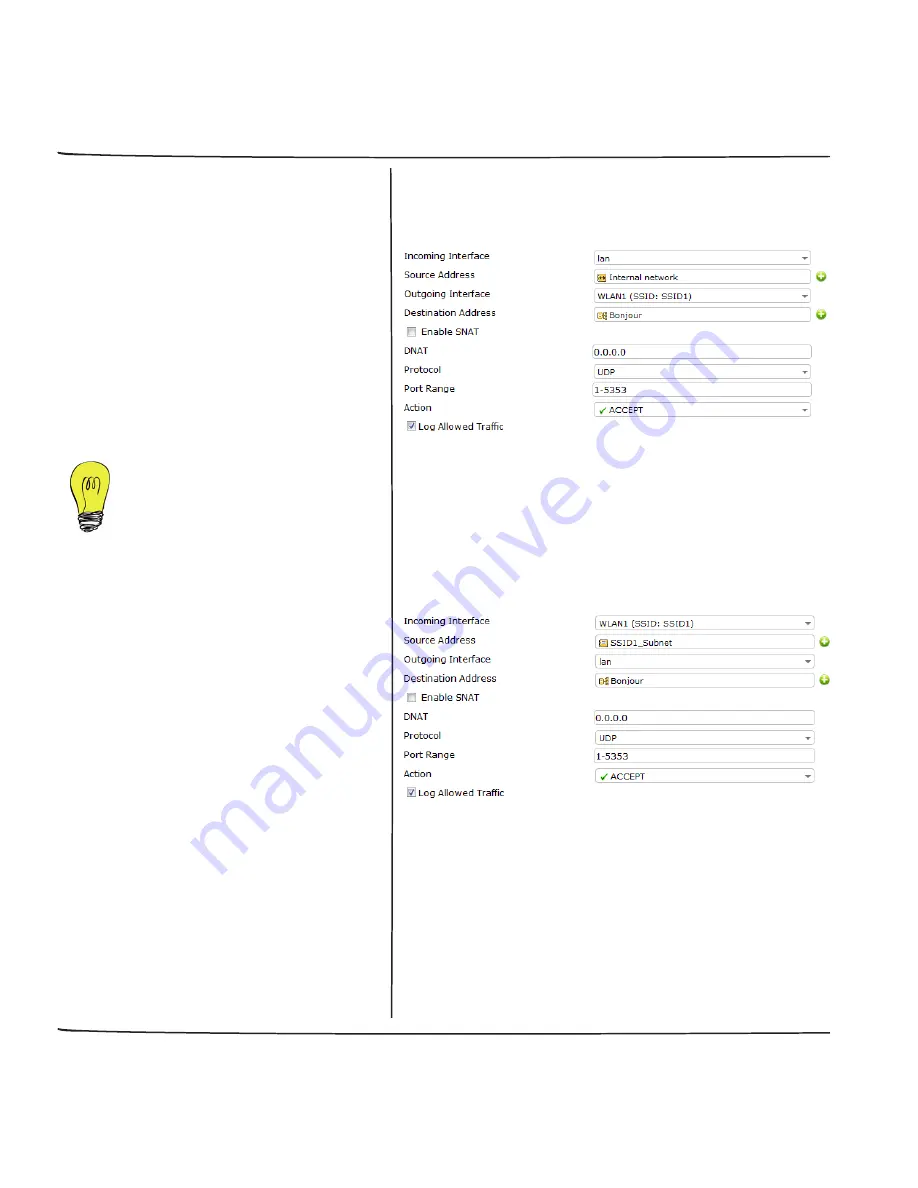
Create a policy to allow multicast traf
fi
c from
the LAN and WLAN1 for AppleTV to iOS
devices. Set
Incoming Interface
to LAN,
Source Address
to the Internal network,
Outgoing Interface
to the SSID, and
Destination Address
to
Bonjour
.
The Bonjour address allows the devices to
fi
nd each other when they connect
through the FortiGate unit.
Go to
Policy > Policy > Multicast Policy
.
Create a policy to allow multicast traf
fi
c
from the WLAN1 and LAN for iOS devices
to AppleTV. Set
Incoming Interface
to
the SSID,
Source Address
to the SSID
IP,
Outgoing Interface
to LAN, and
Destination Address
to
Bonjour
.
Summary of Contents for FortiGate 1U
Page 1: ...FortiOS 5 0 4 1U Models ...
Page 3: ......
Page 4: ...2 ...
Page 5: ...3 QUICKSTART GUIDE FortiGate 1U QuickStart Guide ...
Page 14: ......
Page 15: ...The FortiGate Cookbook Recipes for Success with your FortiGate THE FORTIGATE COOKBOOK ...
Page 16: ......
Page 20: ......
Page 24: ......
Page 88: ......
Page 158: ......
Page 198: ......
Page 229: ...Using redundant OSPF routing over IPsec VPN 209 THE FORTIGATE COOKBOOK ...
Page 235: ...Using redundant OSPF routing over IPsec VPN 215 THE FORTIGATE COOKBOOK ...
Page 238: ......
Page 239: ...About Fortinet High Performace Network Security Q3 2013 ...
Page 253: ...PRODUCT GUIDE Product Guide ...
Page 265: ......








































