154
01-28006-0010-20041105
Fortinet Inc.
RIP
Router
Policy route options
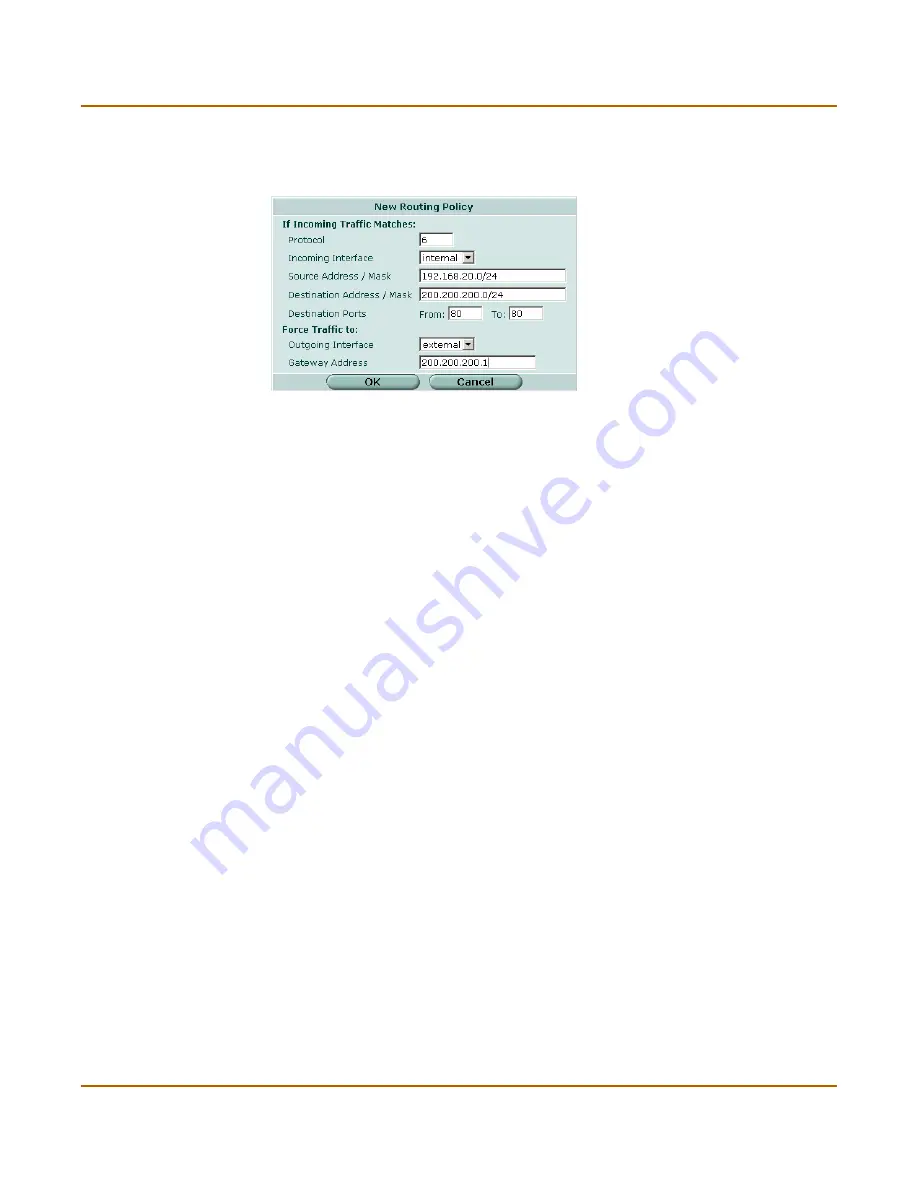
Figure 56: Policy route configuration
To add a policy route
1
Go to
Router > Policy Route
.
2
Select Create New to add a new policy route or select the edit icon beside an existing
policy route to edit that policy route.
3
Optionally enter a Protocol number.
4
Select the Incoming Interface.
5
Enter the Source Address / Mask and the Destination Address / Mask.
6
Optionally enter the Destination Ports.
7
Select the Outgoing Interface.
8
Enter the Gateway Address.
9
Select OK.
RIP
The FortiGate implementation of the Routing Information Protocol (RIP) supports both
RIP version 1 as defined by RFC 1058, and RIP version 2 as defined by RFC 2453.
RIP version 2 enables RIP messages to carry more information, and to support simple
authentication and subnet masks.
Protocol
Match packets that have this protocol number.
Incoming Interface
Match packets that are received on this interface.
Source Address /
Mask
Match packets that have this source IP address and netmask.
Destination
Address / Mask
Match packets that have this destination IP address and netmask.
Destination Ports
Match packets that have this destination port range. To match a single
port, enter the same port number for both From and To.
Outgoing Interface
Send packets that match this policy route, out this interface.
Gateway Address
Send packets that match this policy route to this next hop router.
Summary of Contents for FortiGate 3000
Page 18: ...Contents 18 01 28006 0010 20041105 Fortinet Inc ...
Page 52: ...52 01 28006 0010 20041105 Fortinet Inc Changing the FortiGate firmware System status ...
Page 78: ...78 01 28006 0010 20041105 Fortinet Inc FortiGate IPv6 support System network ...
Page 86: ...86 01 28006 0010 20041105 Fortinet Inc Dynamic IP System DHCP ...
Page 116: ...116 01 28006 0010 20041105 Fortinet Inc FortiManager System config ...
Page 122: ...122 01 28006 0010 20041105 Fortinet Inc Access profiles System administration ...
Page 252: ...252 01 28006 0010 20041105 Fortinet Inc CLI configuration Users and authentication ...
Page 390: ...390 01 28006 0010 20041105 Fortinet Inc Glossary ...
Page 398: ...398 01 28006 0010 20041105 Fortinet Inc Index ...






































