24
01-28008-0111-20050128
Fortinet Inc.
Planning the FortiGate configuration
Getting started
NAT/Route mode
In NAT/Route mode, the FortiGate unit is visible to the network. Like a router, all its
interfaces are on different subnets. The following interfaces are available in
NAT/Route mode:
• Internal is the interface to the internal network.
• WAN1 is the default interface to the external network (usually the Internet).
• WAN2 is the redundant interface to the external network.
• DMZ is the interface to the DMZ network.
• Modem is the interface for connecting an external modem to the FortiGate-60. See
“Configuring the modem interface” on page 57
• Modem is the interface to the FortiGate-60M internal modem. See
“Configuring
modem settings” on page 59
.
You must configure routing to support the redundant WAN1 and WAN2 internet
connections. Routing can be used to automatically redirect connections from an
interface if its connection to the external network fails.
You can add firewall policies to control whether communications through the FortiGate
unit operate in NAT or Route mode. Firewall policies control the flow of traffic based
on the source address, destination address, and service of each packet. In NAT
mode, the FortiGate unit performs network address translation before it sends the
packet to the destination network. In Route mode, there is no address translation.
You typically use NAT/Route mode when the FortiGate unit is operating as a gateway
between private and public networks. In this configuration, you would create NAT
mode firewall policies to control traffic flowing between the internal, private network
and the external, public network (usually the Internet).
If you have multiple internal networks, such as a DMZ network in addition to the
internal, private network, you could create route mode firewall policies for traffic
flowing between them.
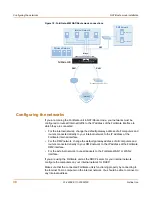
Figure 6: Example NAT/Route mode network configuration
FortiGate-60M Unit
in NAT/Route mode
Route mode policies
controlling traffic between
internal networks.
Internal network
DMZ network
Internal
192.168.1.99
DMZ
10.10.10.1
192.168.1.3
10.10.10.2
WAN1
204.23.1.5
NAT mode policies controlling
traffic between internal and
external networks.
Internet
INTERNAL
DMZ
4
3
2
1
LINK 100
LINK 100
LINK 100
LINK 100
LINK 100
LINK 100
LINK 100
WAN1
WAN2
PWR
STATUS
M