Firmware upgrades
Fortinet Technologies Inc.
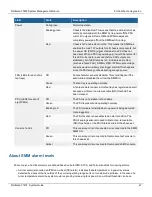
[S]: Set local Subnet Mask
: Set as required for your network.
[G]: Set local gateway
: Set as required for your network.
[V]: Local VLAN ID
: Should be set to
<none>
. (use -1 to set the Local VLAN ID to
<none>
.)
[T]: Set remote TFTP server IP address
: The IP address of the TFTP server.
[F]:
Set firmware image file name
: The name of the firmware image file that you want to install.
12.
To quit this menu, press Q.
13.
To review the configuration, press R.
To make corrections, press C and make the changes as required. When the configuration is correct, proceed to the
next step.
14.
To start the TFTP transfer, press T.
The firmware image is uploaded from the TFTP server and installed on the FIM. The FIM then restarts with its
configuration reset to factory defaults. After restarting, the FIM configuration is synchronized to match the
configuration of the primary FIM. The FIM restarts again and can start processing traffic.
15.
Once the FIM restarts, verify that the correct firmware is installed.
You can do this from the FIM GUI dashboard or from the FIM CLI using the
get system status
command.
16.
Use the
diagnose sys confsync status | grep in_sy
command to verify that the configuration has been
synchronized. The field
in_sync=1
indicates that the configurations of the FIM or FPM is synchronized.
FIMs and FPMs that are missing or that show
in_sync=0
are not synchronized. To synchronize an FIM or FPM
that is not synchronized, log into the CLI of the FIM or FPM and restart it using the
execute reboot
command. If
this does not solve the problem, contact Fortinet Support at
.
If you enter the
diagnose sys confsync status | grep in_sy
command before the FIM has restarted, it
will not appear in the command output. As well, the Configuration Sync Monitor will temporarily show that it is not
synchronized.
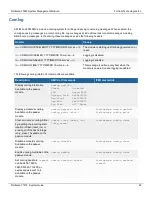
Installing FPM firmware from the BIOS after a reboot
Use the following procedure to upload firmware from a TFTP server to an FPM. To perform the upgrade, you must enter
a command from the primary FIM CLI to allow the FPM BIOS to communicate through an FIM MGMT interface. The
procedure involves creating a connection between the TFTP server and one of the FIM MGMT interfaces.
This procedure also involves connecting to the FPM CLI using a FortiGate-7000F front panel SMM console port,
rebooting the FPM, interrupting the boot from the console session, and following FPM BIOS prompts to install the
firmware.
During this procedure, the FPM will not be able to process traffic. However, the other FPMs and the FIMs should
continue to operate normally.
After you verify that the FPM is running the right firmware, you must log back in to the primary FIM CLI and return the
FPM to normal operation.
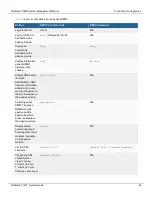
1.
Set up a TFTP server and copy the firmware file into the TFTP server default folder.
2.
Log into to the primary FIM CLI and enter the following command:
diagnose load-balance switch set-compatible <slot> enable bios
Where
<slot>
is the number of the FortiGate-7000F slot containing the FPM to be upgraded.
3.
Set up your network to allow traffic between the TFTP server and a MGMT interface of one of the FIMs.
FortiGate-7121F System Guide
41