264
01-28006-0100-20041105
Fortinet Inc.
PPTP
VPN
4
Add a destination address for the firewall policy.
The destination addresses are the addresses to which the PPTP clients can connect.
For example, if the destination address is on the internal network, you would create an
external-to-internal policy to control the access that PPTP users have through the
FortiGate unit. Typically you would add only one destination address for the entire
internal subnetwork. See
“To add an address” on page 204
.
5
Add an external-to-internal firewall policy.
The firewall policy specifies the source and destination addresses and sets the
service for the policy to the traffic type inside the PPTP VPN tunnel. For example, if
you want PPTP clients to be able to access a web server, set the service to HTTP.
See
“To add a firewall policy” on page 200
.
6
Configure the Windows clients. See:
•
Configuring a Windows 2000 client for PPTP
.
•
Configuring a Windows XP client for PPTP
.
Enabling PPTP and specifying a PPTP range
The PPTP address range is the range of addresses reserved for remote PPTP clients.
When a remote PPTP client connects to the internal network using PPTP, the client
computer is assigned an IP address from this range. The PPTP address range can be
on any subnet.
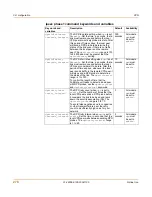
Figure 133:PPTP range
To enable PPTP on the FortiGate unit
1
Go to
VPN > PPTP > PPTP Range
.
2
Select Enable PPTP.
3
Complete the fields as required.
4
Select Apply.
Enable PPTP
You must add a user group before you can enable this option.
Starting IP
The start of the IP range. For example, 192.168.1.10.
Ending IP
The end of the IP range. For example, 192.168.1.20.
User Group
Select the user group that contains the remote PPTP VPN clients.
Disable PPTP
Select this option to disable the PPTP support.
Summary of Contents for FortiGate FortiGate-500A
Page 24: ...24 01 28006 0100 20041105 Fortinet Inc Customer service and technical support Introduction...
Page 46: ...46 01 28006 0100 20041105 Fortinet Inc Changing the FortiGate firmware System status...
Page 72: ...72 01 28006 0100 20041105 Fortinet Inc FortiGate IPv6 support System network...
Page 80: ...80 01 28006 0100 20041105 Fortinet Inc Dynamic IP System DHCP...
Page 110: ...110 01 28006 0100 20041105 Fortinet Inc FortiManager System config...
Page 116: ...116 01 28006 0100 20041105 Fortinet Inc Access profiles System administration...
Page 134: ...134 01 28006 0100 20041105 Fortinet Inc Shutdown System maintenance...
Page 248: ...248 01 28006 0100 20041105 Fortinet Inc CLI configuration Users and authentication...
Page 324: ...324 01 28006 0100 20041105 Fortinet Inc CLI configuration Antivirus...
Page 386: ...386 01 28006 0100 20041105 Fortinet Inc Glossary...
Page 394: ...394 01 28006 0100 20041105 Fortinet Inc Index...