VPN
Configuring IPSec virtual IP addresses
FortiGate-500A Administration Guide
01-28006-0100-20041105
293
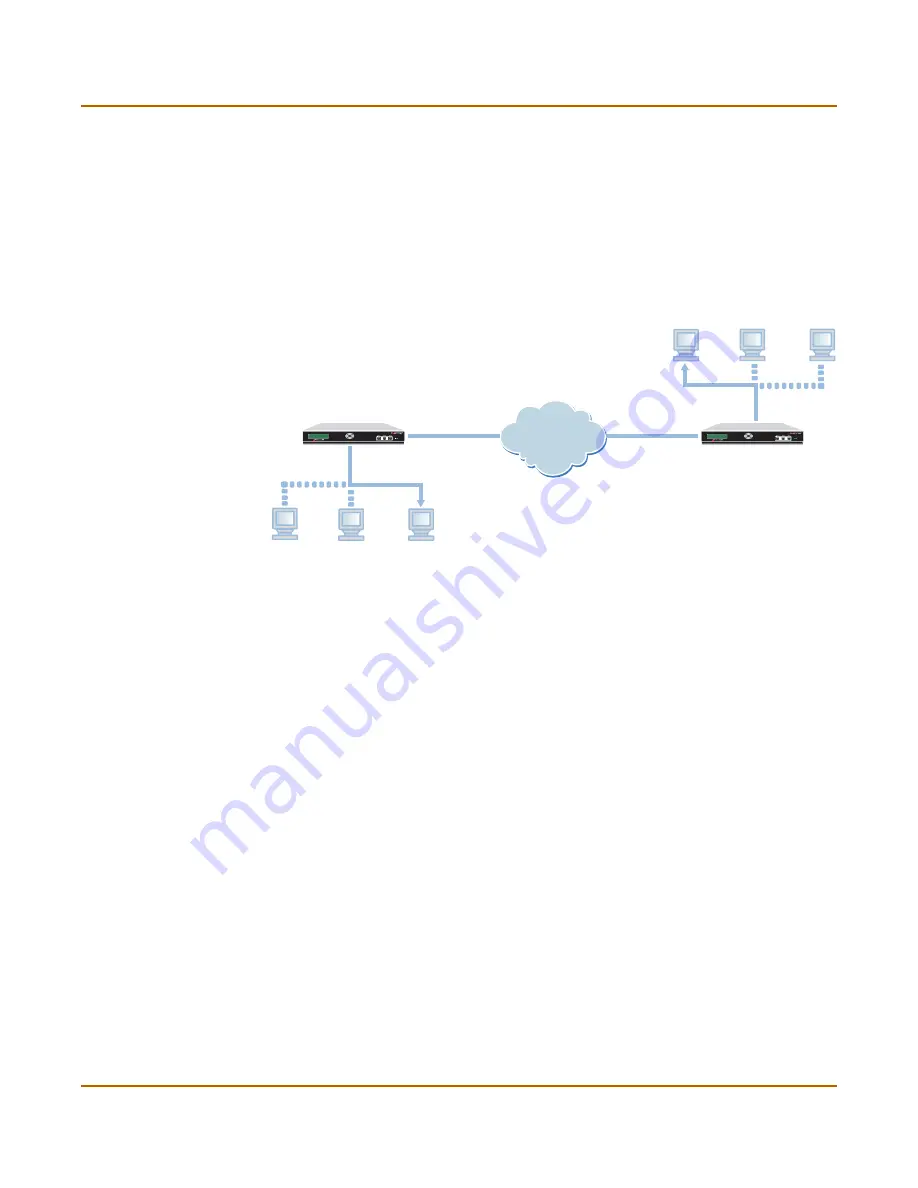
Consider the following example, which shows two physically separate networks. The
IP addresses of the computers on both networks are in the 192.168.12.0/24 range,
but no two IP addresses are the same. An IPSec VPN has been configured between
FortiGate_1 and FortiGate_2. The FortiGate configuration permits Host_1 on the
Finance network to transmit data to Host_2 on the HR network through the IPSec
VPN tunnel.
Figure 140:A typical site-to-site configuration using the IPSec VIP feature
When Host_1 attempts to send a packet to Host_2 for the first time, Host_1 issues an
ARP request locally for the MAC address of Host_2. However, because Host_2
resides on a remote network, it does not respond. Instead, the FortiGate unit
responds with its own MAC address. From that point, Host_1 adds the MAC address
of the FortiGate unit to its ARP cache and the FortiGate unit will act as a proxy for
Host_2.
In the above example, the private IP addresses between the two sites have been
coordinated to protect against ambiguous routing (no two IP addresses are the same).
Setting up a configuration like this involves performing the following tasks at
FortiGate_1 and FortiGate_2:
To enable IPSec VPN communication between two network hosts that coordinate the
same private address space on physically separate networks, perform the following
tasks at the local and remote FortiGate units:
1
On both FortiGate units, define the gateway/tunnel on which to transmit VPN traffic to
the remote location (see
“Phase 1” on page 250
and
“Phase 2” on page 254
).
2
On both FortiGate units, define the firewall encrypt policy that is needed to select and
enable communication through the defined VPN gateway/tunnel (see
“Firewall” on
page 193
).
3
Using CLI commands to configure the local FortiGate unit, add VIP entries to define
which IP addresses can be accessed at the remote end of the VPN tunnel (see
“ipsec
vip” on page 280
). For example, to enable access to Host_2 on the HR network from
Host_1 on the Finance network, enter the following CLI commands on FortiGate_1:
Esc
Enter
Host_2
192.168.12.2
external
Host_1
192.168.12.1
FortiGate_1
external
Esc
Enter
FortiGate_2
Finance Network
192.168.12.0/24
HR Network
192.168.12.0/24
Internet
Summary of Contents for FortiGate FortiGate-500A
Page 24: ...24 01 28006 0100 20041105 Fortinet Inc Customer service and technical support Introduction...
Page 46: ...46 01 28006 0100 20041105 Fortinet Inc Changing the FortiGate firmware System status...
Page 72: ...72 01 28006 0100 20041105 Fortinet Inc FortiGate IPv6 support System network...
Page 80: ...80 01 28006 0100 20041105 Fortinet Inc Dynamic IP System DHCP...
Page 110: ...110 01 28006 0100 20041105 Fortinet Inc FortiManager System config...
Page 116: ...116 01 28006 0100 20041105 Fortinet Inc Access profiles System administration...
Page 134: ...134 01 28006 0100 20041105 Fortinet Inc Shutdown System maintenance...
Page 248: ...248 01 28006 0100 20041105 Fortinet Inc CLI configuration Users and authentication...
Page 324: ...324 01 28006 0100 20041105 Fortinet Inc CLI configuration Antivirus...
Page 386: ...386 01 28006 0100 20041105 Fortinet Inc Glossary...
Page 394: ...394 01 28006 0100 20041105 Fortinet Inc Index...
















































