274
01-28007-0144-20041217
Fortinet Inc.
CLI configuration
VPN
ipsec vip
A FortiGate unit can act as a proxy by answering ARP requests locally and forwarding
the associated traffic to the intended destination host over an IPSec VPN tunnel. The
feature is intended to enable IPSec VPN communications between two hosts that
coordinate the same private address space on physically separate networks. The IP
addresses of both the source host and the destination host must be unique. The
ipsec vip
command lets you specify the IP addresses that can be accessed at the
remote end of the VPN tunnel. You must configure IPSec virtual IP (VIP) addresses at
both ends of the IPSec VPN tunnel.
Adding an IPSec VIP entry to the VIP table enables a FortiGate unit to respond to
ARP requests destined for remote servers and route traffic to the intended
destinations automatically. Each IPSec VIP entry is identified by an integer. An entry
identifies the name of the FortiGate interface to the destination network, and the IP
address of a destination host on the destination network. Specify an IP address for
every host that needs to be accessed on the other side of the tunnel—you can define
a maximum of 32 IPSec VIP addresses on the same interface.
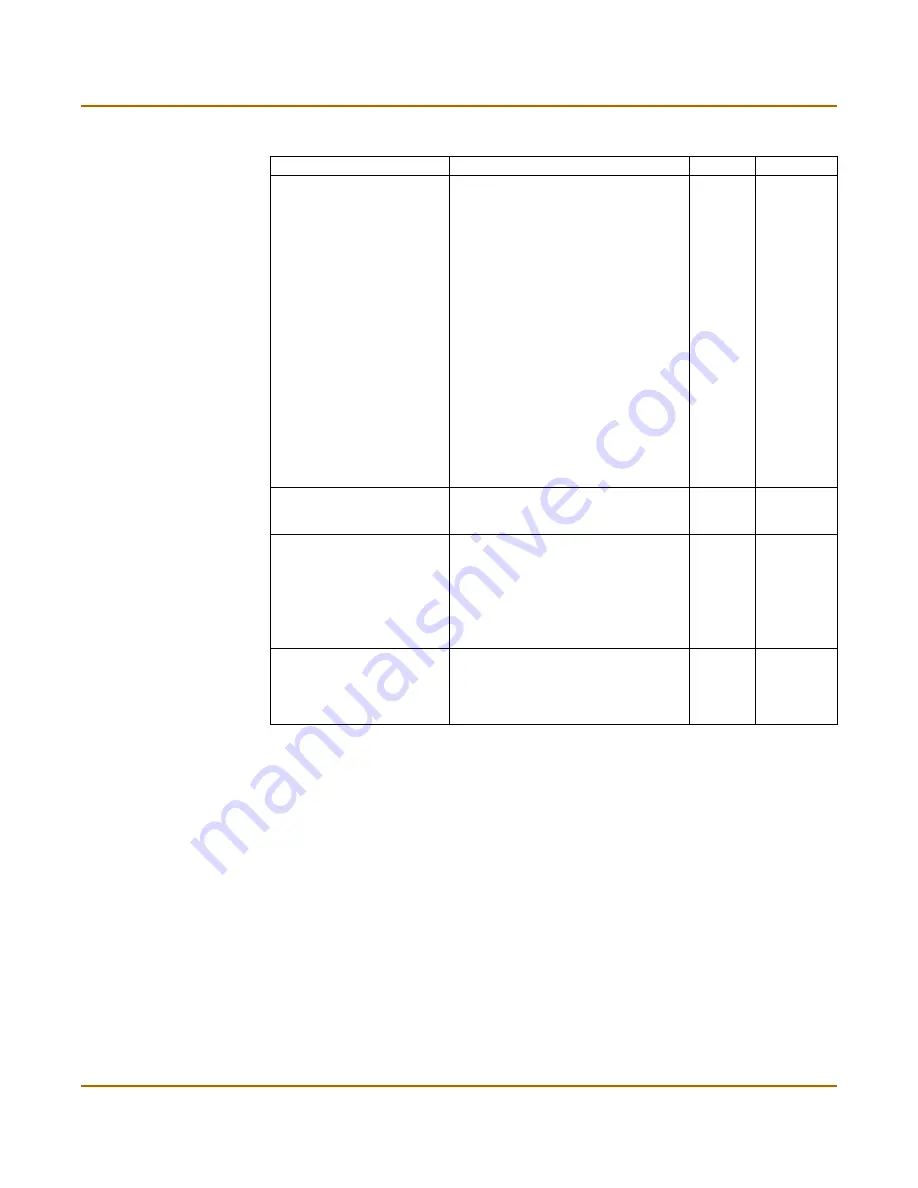
selector { policy |
wildcard | specify}
Enter the method for choosing
selectors for IKE negotiations:
• Select
policy
to choose a selector
from a firewall encryption policy. The
VPN tunnel referenced in the firewall
encryption policy will be referenced.
• Select
wildcard
to disable selector
negotiation for this tunnel. Use this
option to avoid negotiation errors
(such as invalid ID Information) that
may occur during quick mode when
the set of policies between the peers
is not symmetric.
• Select
specify
to specify the
firewall encryption policy source and
destination IP addresses, ports, and
IP protocol to use for selector
negotiation. When you choose
specify
, you must also enter
values for the
srcaddr
,
dstaddr
,
protocol
,
srcport
, and
dstport
keywords.
policy
All models.
single-source
{disable | enable}
Enable or disable all dialup clients to
connect using the same phase 2
tunnel definition.
disable
All models.
srcaddr <name_str>
Enter the name of the firewall source
IP address that corresponds to the
local sender or network behind the
local VPN peer.
You must create the
firewall address before you can select
it here. For more information, see
“Adding firewall policies for IPSec VPN
tunnels” on page 268
.
No
default.
All models.
selector
must be set
to
specify
.
srcport
<port_integer>
Enter the port number that the local
VPN peer uses to transport traffic
related to the specified service (see
protocol
). The
srcport
range is
1
to
65535
. To specify all ports, type
0
.
No
default.
All models.
selector
must be set
to
specify
.
ipsec phase2 command keywords and variables (Continued)
Keywords and variables
Description
Default
Availability
Summary of Contents for FortiGate FortiGate-60M
Page 12: ...Contents 12 01 28007 0144 20041217 Fortinet Inc Index 369 ...
Page 44: ...44 01 28007 0144 20041217 Fortinet Inc Changing the FortiGate firmware System status ...
Page 74: ...74 01 28007 0144 20041217 Fortinet Inc FortiGate IPv6 support System network ...
Page 82: ...82 01 28007 0144 20041217 Fortinet Inc Dynamic IP System DHCP ...
Page 116: ...116 01 28007 0144 20041217 Fortinet Inc Access profiles System administration ...
Page 234: ...234 01 28007 0144 20041217 Fortinet Inc Protection profile Firewall ...
Page 246: ...246 01 28007 0144 20041217 Fortinet Inc CLI configuration Users and authentication ...
Page 278: ...278 01 28007 0144 20041217 Fortinet Inc CLI configuration VPN ...
Page 340: ...340 01 28007 0144 20041217 Fortinet Inc Using Perl regular expressions Spam filter ...
Page 358: ...358 01 28007 0144 20041217 Fortinet Inc CLI configuration Log Report ...
Page 376: ...376 01 28007 0144 20041217 Fortinet Inc Index ...


































