P O L I C Y C O N F I G U R A T I O N
About Security Policies
9-2
Security Appliance User Guide
Version 3R2
9
If the source and destination zones are the same, then the CARD2-G
software searches intrazone policies first. If there is no match, then the
software searches global policies. If there is still no match, the software
applies a default zone policy that drops the packet.
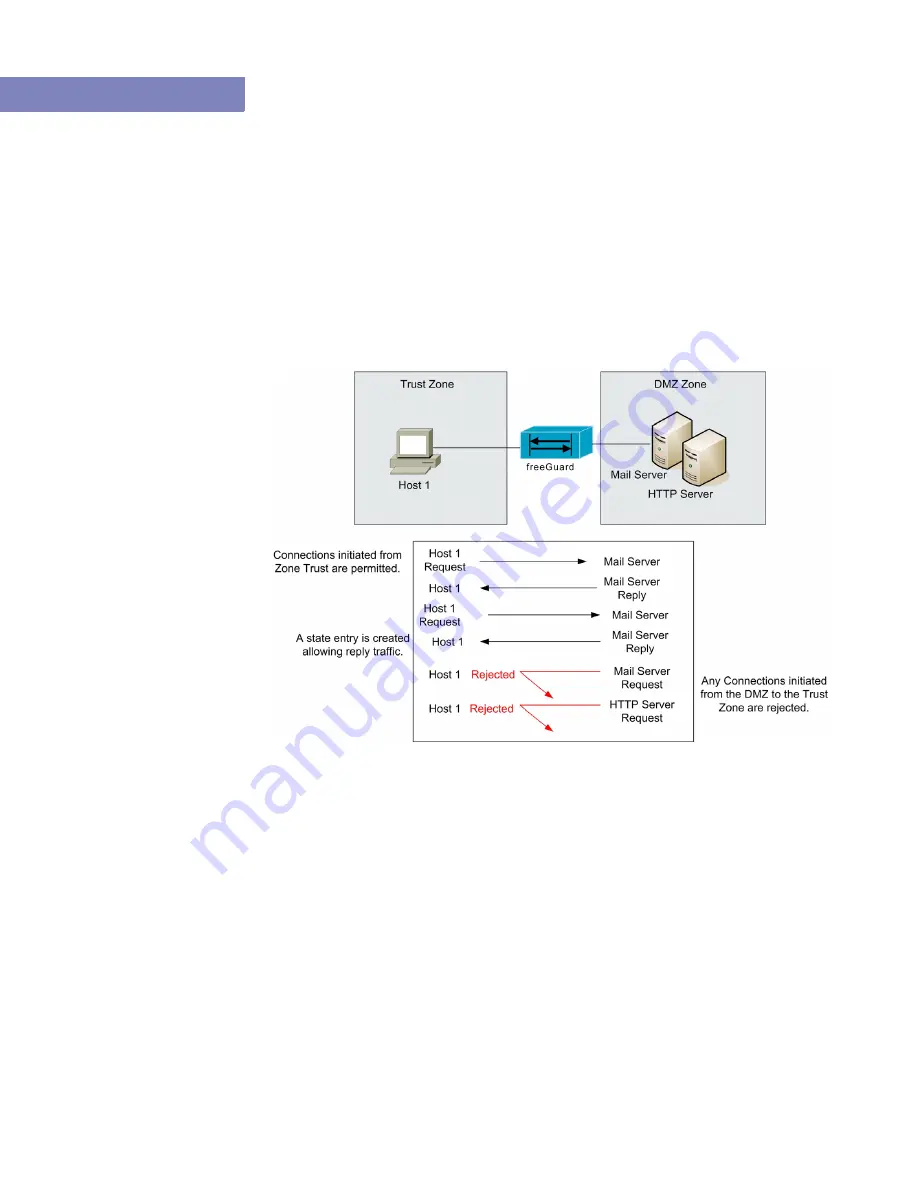
Figure 9-1
displays the use of security policies.
Figure 9-1: Security Policies
ABOUT SECURITY POLICY TYPES
You can configure three types of policies for the appliance:
•
Interzone Policy. Refer to
Configuring Interzone Policies
.
• Intrazone Policies. Refer to
Configuring Intrazone Policies
.
• Global Policies. Refer to
Configuring Global Policies
.
C O N F I G U R I N G I N T E R Z O N E P O L I C I E S
An interzone policy controls traffic between zones. These policies can
allow, deny, or reject traffic that is to pass from one zone and destined
for another. For example, in
Figure 9-2
, the appliance is configured with
a policy that allows HTTP traffic initiated from Host A in the trust zone to
Server B in the untrust zone using the following command:







































