Chapter
9
9 – Access Using
Using a server to authenticate access….
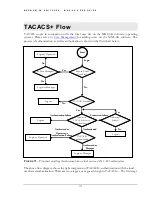
his feature is available in MNS-6K-SECURE. , short for Terminal Access
Controller Access Control System, protocol provides access control for routers, network
access servers and other networked computing devices via one or more centralized servers.
provides separate authentication, authorization and accounting services.
T
T
T
a
ACACS – flavors and history
ACACS allows a client to accept a username and password and send a query to
TACACS authentication server, sometimes called a TACACS daemon (server)
or simply TACACSD. This server was normally a program running on a host.
The host would determine whether to accept or deny the request and sent a response back.
j
The protocol is the latest generation of TACACS. TACACS is a simple UDP based
access control protocol originally developed by BBN for the MILNET (Military Network).
Cisco’s enhancements to TACACS are called XTACACS. XTACACS is now replaced by
. is a TCP
based access control protocol. TCP offers a reliable connection-
oriented transport, while UDP offers best-effort delivery.
improves on TACACS and XTACACS by separating the functions of
authentication, authorization and accounting and by encrypting all traffic between the Network
Access Server (NAS) and the clients or services or daemon. It allows for arbitrary
length and content authentication exchanges, which allows any authentication mechanism to be
utilized with clients. The protocol allows the client to request very fine-
grained access control by responding to each component of a request.
The Magnum 6K family of switches implements a client.
1.
servers and daemons use TCP Port 49 for listening to client
requests. Clients connect to this port number to send authentication and
authorization packets.
2.
There can be more than one server on the network. MNS-
6K supports a maximum of five servers
116