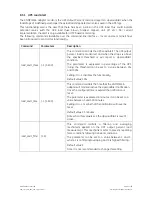
7.2 SERVICES (ACCESS METHODS)
The table below lists the available services (access methods), highlighting the major security features for
each interface.
Interface Access
methods
Security
features
Local console interface
Serial cable
Authentication via user/pwd pair
Telnet Authentication via user/pwd pair
Plain text
Remote console interface
SSH (Secure SHell)
Authentication via user/pwd pair
Encrypted communication
SNMP Agent
SNMP Community
Name
Plain text
FTP
Authentication via user/pwd pair
Plain text
File transfer
SFTP (SSH FTP)
Authentication via user/pwd pair
Encrypted communication
HTTP
Authentication via user/pwd pair
Plain text
Web interface
HTTPS (SSL)
Authentication via user/pwd pair
Encrypted communication
7.3 ENCRYPTION
As stated above, the SNMP/Web adapter offers interfaces providing encryption for protecting data
confidentiality and integrity, and particularly the following:
•
SSH (Secure Shell)
•
SFTP (SSH File Transfer Protocol)
•
HTTPS
In this context, encryption is based on public-key cryptography schemes. Normally, the SNMP/Web
adapters will be delivered already configured with all applicable keys and certificates – should the
adapter miss these information it will generate them at first start-up (this operation may take some
time). The length of the keys used for encryption is 1024 bits, providing complex encryption and a
higher level of security.
7.3.1 SSH and SFTP
SSH
allows running terminal sessions to the SNMP/Web adapter over a secure channel. SSH uses public-
key cryptography. The SSH server is authenticated using a host key as identification. Most SSH clients
display the host key fingerprint at the start of the SSH session. Below is an example from a popular SSH
client (putty):
Modifications reserved
Page 45/58
OPM_CNT_SNM_BAS_CRD_1GB_V012.doc
Operating Manual
SNMP/Web Adapter