5
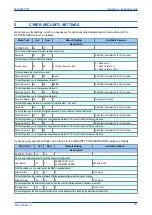
CYBER-SECURITY SETTINGS
General security settings, which are necessary for cyber-security implementation can be found in the
SYSTEM DATA column as follows:
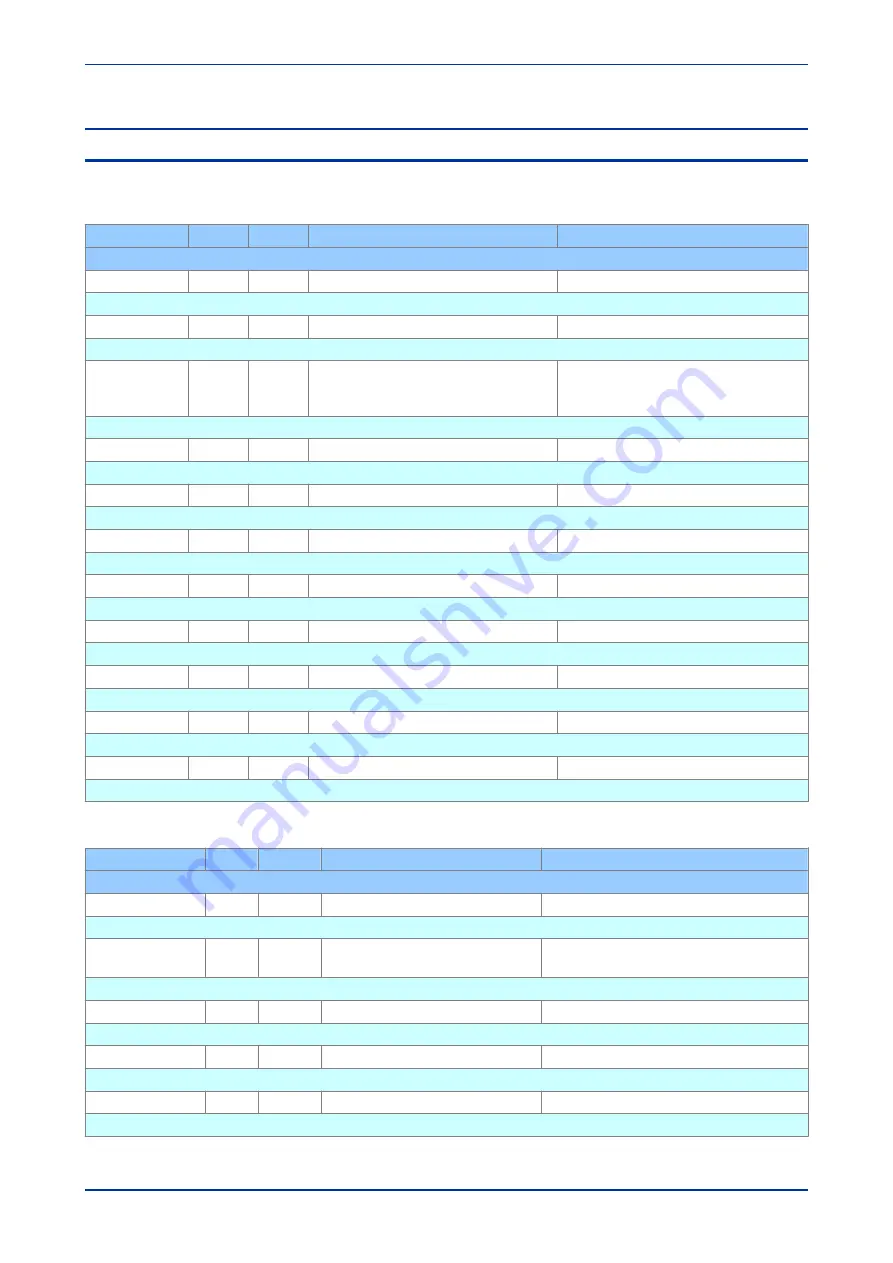
Menu Text
Col
Row
Default Setting
Available Options
Description
SYSTEM DATA
00
00
This column contains general system settings and records.
Password
00
02
ASCII text (characters 33 to 122 inclusive)
This setting sets the device default password
Access Level
00
D0
2 = Read + E Edit
0 = Read only or
1 = Read + Execute, or
2 = Read + E Edit
This cell displays the current access level.
Password Level 1
00
D2
blank
ASCII text (characters 33 to 122 inclusive)
This setting allows you to change password level 1.
Password Level 2
00
D3
BBBB
ASCII text (characters 33 to 122 inclusive)
This setting allows you to change password level 2.
Password Level 3
00
D4
AAAA
ASCII text (characters 33 to 122 inclusive)
This setting allows you to change password level 3.
Security Features
00
DF
1
{cyber-security level}
This setting displays the level of cyber-security implemented, 1 = phase 1.
Password
00
E1
ASCII text (characters 33 to 122 inclusive)
This cell allows you to enter the encrypted password. It is not visible via the user interfaced.
Password Level 1
00
E2
ASCII text (characters 33 to 122 inclusive)
This setting allows you to change the encrypted password level 1. This is not visible via the user interface.
Password Level 2
00
E3
ASCII text (characters 33 to 122 inclusive)
This setting allows you to change the encrypted password level 2. This is not visible via the user interface.
Password Level 3
00
E4
ASCII text (characters 33 to 122 inclusive)
This setting allows you to change the encrypted password level 3. This is not visible via the user interface.
Cyber-security specific settings can be found in the SECURITY CONFIGURATION column as follows:
Menu Text
Col
Row
Default Setting
Available Options
Description
SECURITY CONFIG
25
00
This column contains settings for the Cyber-Security configuration
User Banner
25
01
ACCESS ONLY FOR
AUTHORISED USERS
ASCII 32 to 234
With this setting, you can enter text for the NERC compliant banner.
Attempts Limit
25
02
2
0 to 3 step 1
This setting defines the maximum number of failed password attempts before action is taken.
Attempts Timer
25
03
2
1 to 3 step 1
This setting defines the time window used in which the number of failed password attempts is counted.
Blocking Timer
25
04
5
1 to 30 step 1
This setting defines the time duration for which the user is blocked, after exceeding the maximum attempts limit.
MiCOM P747
Chapter 9 - Cyber-Security
P747-TM-EN-1
291
P747-TM-EN-1.1
Summary of Contents for MiCOM P747 Agile
Page 2: ......
Page 16: ...Contents MiCOM P747 xiv P747 TM EN 1 P747 TM EN 1 1...
Page 20: ...Table of Figures MiCOM P747 xviii P747 TM EN 1 P747 TM EN 1 1...
Page 21: ...INTRODUCTION CHAPTER 1...
Page 22: ...Chapter 1 Introduction MiCOM P747 2 P747 TM EN 1 P747 TM EN 1 1...
Page 31: ...SAFETY INFORMATION CHAPTER 2...
Page 32: ...Chapter 2 Safety Information MiCOM P747 12 P747 TM EN 1 P747 TM EN 1 1...
Page 42: ...Chapter 2 Safety Information MiCOM P747 22 P747 TM EN 1 P747 TM EN 1 1...
Page 43: ...HARDWARE DESIGN CHAPTER 3...
Page 44: ...Chapter 3 Hardware Design MiCOM P747 24 P747 TM EN 1 P747 TM EN 1 1...
Page 74: ...Chapter 3 Hardware Design MiCOM P747 54 P747 TM EN 1 P747 TM EN 1 1...
Page 75: ...CONFIGURATION CHAPTER 4...
Page 76: ...Chapter 4 Configuration MiCOM P747 56 P747 TM EN 1 P747 TM EN 1 1...
Page 117: ...PROTECTION FUNCTIONS CHAPTER 5...
Page 118: ...Chapter 5 Protection Functions MiCOM P747 98 P747 TM EN 1 P747 TM EN 1 1...
Page 160: ...Chapter 5 Protection Functions MiCOM P747 140 P747 TM EN 1 P747 TM EN 1 1...
Page 161: ...MONITORING AND CONTROL CHAPTER 6...
Page 162: ...Chapter 6 Monitoring and Control MiCOM P747 142 P747 TM EN 1 P747 TM EN 1 1...
Page 211: ...SCADA COMMUNICATIONS CHAPTER 7...
Page 212: ...Chapter 7 SCADA Communications MiCOM P747 192 P747 TM EN 1 P747 TM EN 1 1...
Page 259: ...REDUNDANT ETHERNET CHAPTER 8...
Page 260: ...Chapter 8 Redundant Ethernet MiCOM P747 240 P747 TM EN 1 P747 TM EN 1 1...
Page 293: ...CYBER SECURITY CHAPTER 9...
Page 294: ...Chapter 9 Cyber Security MiCOM P747 274 P747 TM EN 1 P747 TM EN 1 1...
Page 313: ...SETTINGS APPLICATION SOFTWARE CHAPTER 10...
Page 314: ...Chapter 10 Settings Application Software MiCOM P747 294 P747 TM EN 1 P747 TM EN 1 1...
Page 322: ...Chapter 10 Settings Application Software MiCOM P747 302 P747 TM EN 1 P747 TM EN 1 1...
Page 323: ...BUSBAR COMMISSIONING TOOL CHAPTER 11...
Page 324: ...Chapter 11 Busbar Commissioning Tool MiCOM P747 304 P747 TM EN 1 P747 TM EN 1 1...
Page 330: ...Chapter 11 Busbar Commissioning Tool MiCOM P747 310 P747 TM EN 1 P747 TM EN 1 1...
Page 331: ...SCHEME LOGIC CHAPTER 12...
Page 332: ...Chapter 12 Scheme Logic MiCOM P747 312 P747 TM EN 1 P747 TM EN 1 1...
Page 348: ...Chapter 12 Scheme Logic MiCOM P747 328 P747 TM EN 1 P747 TM EN 1 1...
Page 349: ...INSTALLATION CHAPTER 13...
Page 350: ...Chapter 13 Installation MiCOM P747 330 P747 TM EN 1 P747 TM EN 1 1...
Page 361: ...COMMISSIONING INSTRUCTIONS CHAPTER 14...
Page 362: ...Chapter 14 Commissioning Instructions MiCOM P747 342 P747 TM EN 1 P747 TM EN 1 1...
Page 387: ...MAINTENANCE AND TROUBLESHOOTING CHAPTER 15...
Page 388: ...Chapter 15 Maintenance and Troubleshooting MiCOM P747 368 P747 TM EN 1 P747 TM EN 1 1...
Page 403: ...TECHNICAL SPECIFICATIONS CHAPTER 16...
Page 404: ...Chapter 16 Technical Specifications MiCOM P747 384 P747 TM EN 1 P747 TM EN 1 1...
Page 425: ...SYMBOLS AND GLOSSARY APPENDIX A...
Page 426: ...Appendix A Symbols and Glossary MiCOM P747 406 P747 TM EN 1 P747 TM EN 1 1...
Page 443: ...COMMISSIONING RECORD APPENDIX B...
Page 444: ...Appendix B Commissioning Record MiCOM P747 424 P747 TM EN 1 P747 TM EN 1 1...
Page 449: ...WIRING DIAGRAMS APPENDIX C...
Page 450: ...Appendix C Wiring Diagrams MiCOM P747 430 P747 TM EN 1 P747 TM EN 1 1...
Page 456: ...Appendix C Wiring Diagrams MiCOM P747 436 P747 TM EN 1 P747 TM EN 1 1...
Page 457: ......