Authentication and its Application
14
2
About Administrator Authentication
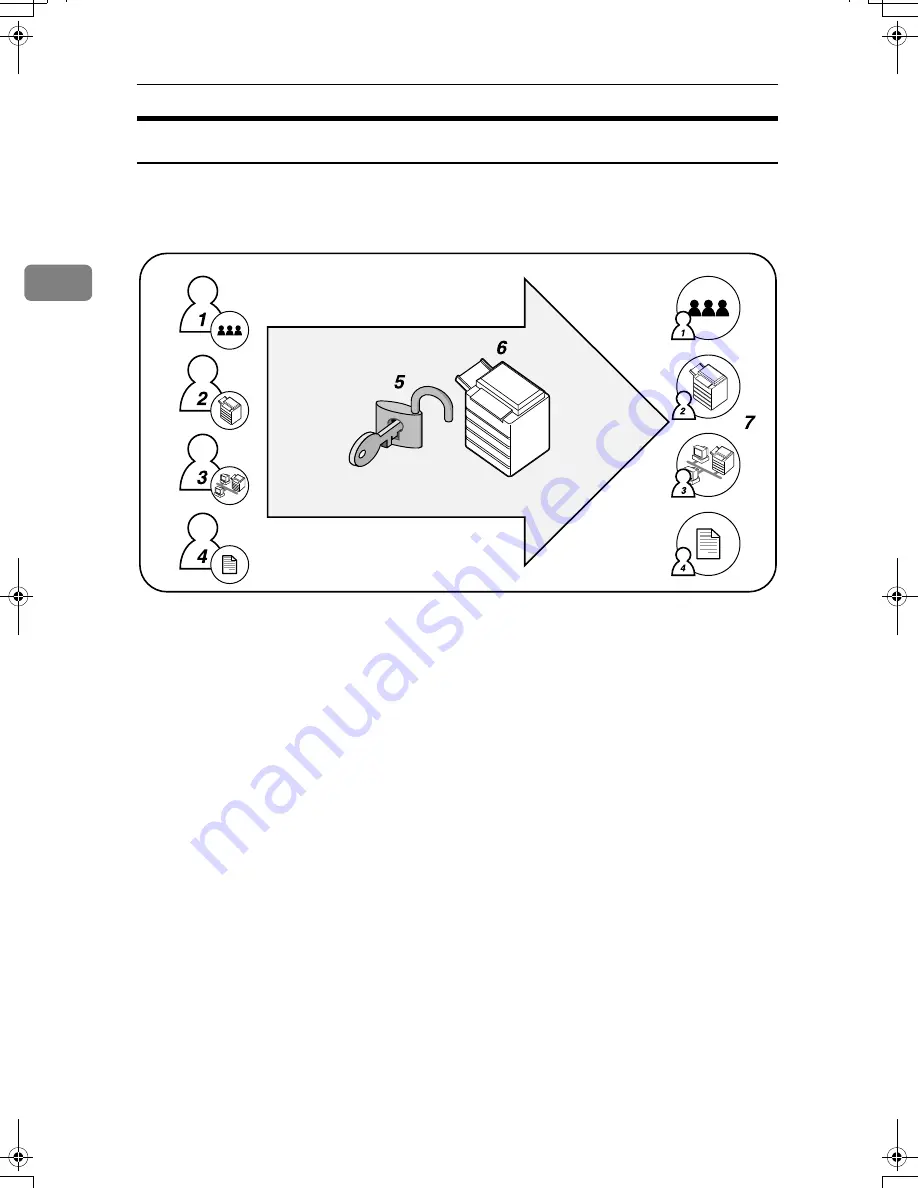
There are four types of administrator: user administrator, machine administra-
tor, network administrator, and file administrator.
1.
User Administrator
This administrator manages personal in-
formation in the address book. You can
register/delete users in the address book
or change users’ personal information.
2.
Machine Administrator
This administrator manages the ma-
chine’s default settings. It is possible to
enable only the machine administrator to
set deta security for copying, log deletion
and other defaults.
3.
Network Administrator
This administrator manages the network
settings. You can set the machine so that
network settings such as the IP address
and settings for sending and receiving e-
mail can be specified by the network ad-
ministrator only.
4.
File Administrator
This administrator manages permission
to access stored files. You can specify
passwords for Locked Print files stored in
the Document Server so only authorized
users can view and change them.
5.
Authentication
Administrators must enter their login
user name and password to be authenti-
cated.
6.
This machine
7.
Administrators manage the ma-
chine’s settings and access limits.
For details about each administrator,
see p.11 “Administrators”.
AYJ002S
D0086951_RussianC45-EN.book Page 14 Wednesday, May 31, 2006 11:45 AM
Summary of Contents for DSm725e
Page 8: ...2...






































