P a g e
|
16
UCM Security Manual
Please configure the privilege for the outbound rule high enough to restrict the extensions allowed to call
external numbers via this trunk.
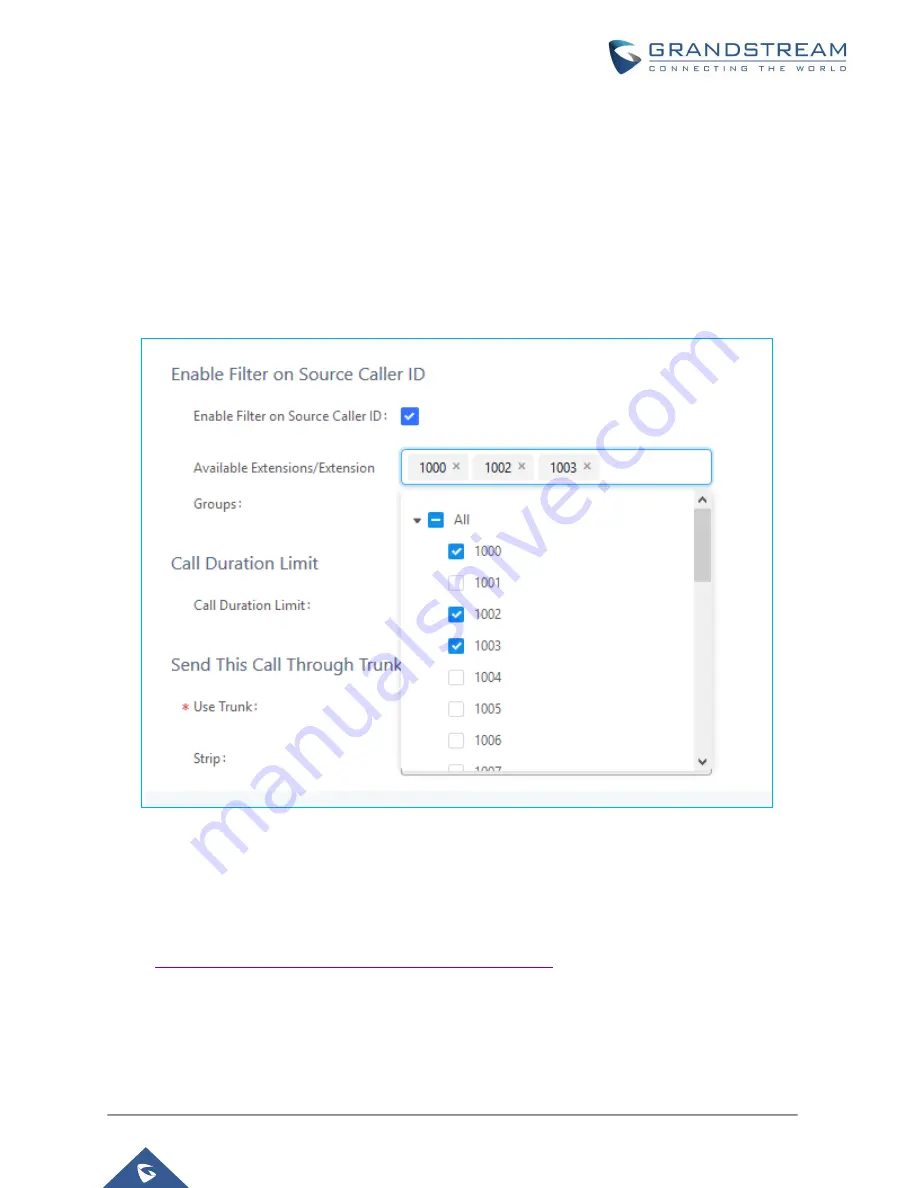
Source Caller ID Filter
Instead of using privilege level, UCM administrator could specify the extensions/extension groups that are
allowed to use the outbound rule. This can be done by selecting extension/extension groups or defining
pattern for the source caller ID in “Custom Dynamic Route” field. The extension allowed to make outbound
call will either need to be an extension in the selected list or match the defined pattern.
Figure 10: Source Caller ID Filter
Please specify the extension or the pattern here to the minimal set so that only the desired users can dial
out from this outbound route.
For detailed configuration instructions, please refer to MANAGING OUTBOUND ROUTE section in white
paper:
How to manage inbound/outbound route on UCM6510/6100
Password protection
For even more security, users could protect the outbound rule with a password that will be requested by
the UCM from the callers in order to allow outbound calls. Users can set the password on each outbound
on the specified field as shown on the figure below.
















































