163
Configuring VPLS
This chapter describes how to configure VPLS.
The S5500-28SC-HI and S5500-52SC-HI switches do not support VPLS.
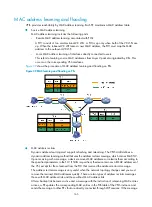
VPLS overview
Virtual Private LAN Service (VPLS), also called "Transparent LAN Service (TLS)" or "virtual private
switched network service," can deliver a point-to-multipoint L2VPN service over public networks. With
VPLS, geographically-dispersed sites can interconnect and communicate over MAN or WAN as if they
were on the same LAN.
VPLS provides Layer 2 VPN services. However, it supports multipoint services rather than the
point-to-point services the traditional VPN supports. With VPLS, service providers can create a series of
virtual switches for customers on the PEs, allowing customers to build their LANs across the MAN or
WAN.
Basic VPLS concepts
•
CE
—Customer edge device. A CE is directly connected to the PE.
•
PE
—Provider edge device. A PE connects one or more CEs to the service provider network. It maps
and forwards packets between private networks and public network tunnels. A PE can be a UPE or
NPE.
•
UPE
—User facing provider edge device. A UPE functions as the user access convergence device.
•
NPE
—Network provider edge device. An NPE functions as the network core PE, resides at the edge
of a VPLS network core domain, and provides transparent VPLS transport services between core
networks.
•
VSI
—Virtual switch instances (hereinafter referred to as "VPLS instances") maps actual access links
to virtual links.
•
PW
—A pseudo wire is a bidirectional virtual connection between VSIs. A PW consists of two
unidirectional MPLS virtual circuits (VCs) with opposite directions.
•
Service instance
—A service instance is created on a port to identify and process packets passing
through the port. A PE uses service instances to match traffic received from a CE, so as to forward
the traffic with different characteristics over different PWs. A service instance supports multiple
packet matching rules, providing flexible VPLS access.
•
AC
—An attachment circuit connects a CE to a PE. It can use physical interfaces or virtual interfaces.
Usually, all user packets on an AC, including Layer 2 and Layer 3 protocol messages, must be
forwarded to the peer site without being changed. On the switch, each service instance on a port
corresponds one AC.
•
QinQ
—802.1Q in 802.1Q. It is a tunneling protocol based on 802.1Q. It offers a
point-to-multipoint L2VPN service mechanism. With QinQ, the private network VLAN tags of
packets are encapsulated into the public network VLAN tags, allowing packets to be transmitted
with two layers of tags across the service provider network. This provides a simpler Layer 2 VPN
tunneling service.