97
No Agreement Check configuration example
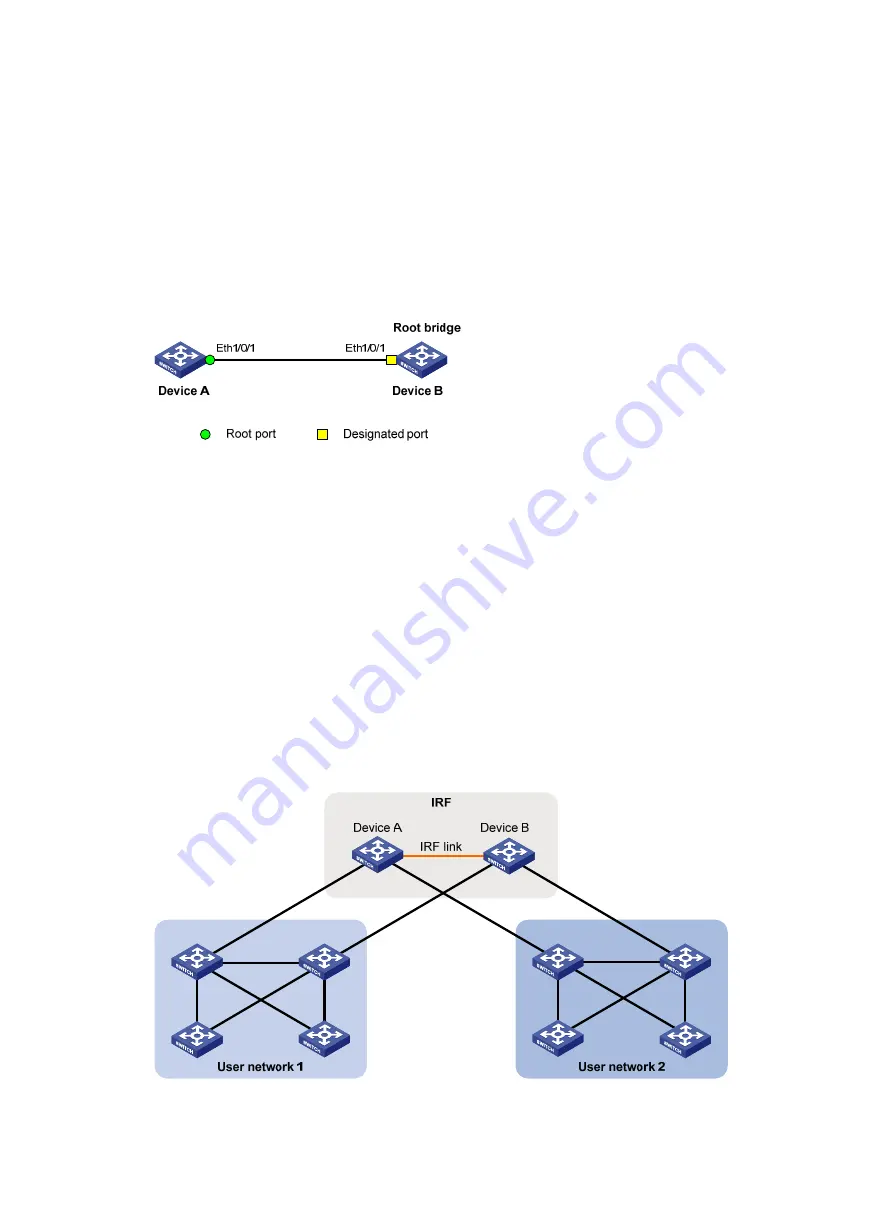
Network requirements
As shown in
:
•
Device A connects to a third-party device that has a different spanning tree implementation. Both
devices are in the same region.
•
The third-party device (Device B) is the regional root bridge, and Device A is the downstream
device.
Figure 28
Network diagram
Configuration procedure
# Enable No Agreement Check on Ethernet 1/0/1 of Device A.
<DeviceA> system-view
[DeviceA] interface ethernet 1/0/1
[DeviceA-Ethernet1/0/1] stp no-agreement-check
Configuring TC snooping
shows a topology change (TC) snooping application scenario. Device A and Device B form an
IRF fabric and do not have the spanning tree feature enabled. The IRF fabric connects to two user
networks, in which all devices are enabled with the spanning tree feature. The user networks are
dual-uplinked to the IRF fabric for high availability. The IRF fabric transparently transmits BPDUs in every
user network.
Figure 29
TC snooping application scenario
















































