9-2
clients, ports that connect to DHCP clients, and VLANs to which the ports belong. With DHCP
snooping entries, DHCP snooping can implement the following:
z
ARP detection: Whether ARP packets are sent from an authorized client is determined based on
DHCP snooping entries. This feature prevents ARP attacks from unauthorized clients. For details,
see ARP Attack Protection Configuration in the Security Configuration Guide
.
z
MAC-forced forwarding (MFF): In automatic mode, after receiving an ARP request from a client,
the MFF device searches DHCP snooping entries for the corresponding gateway address, and
sends it to the client. This feature allows the gateway to monitor client traffic, prevents malicious
attacks among clients, and therefore guarantees network security. For details,
see MFF
Configuration in the Security Configuration Guide
.
z
IP Source Guard: IP Source Guard uses dynamic binding entries generated by DHCP snooping
to filter packets on a per-port basis, and thus prevents unauthorized packets from traveling
through. For details,
see IP Source Guard Configuration in the Security Configuration Guide
.
z
VLAN mapping: The device replaces service provider VLANs (SVLANs) in packets with customer
VLANs (CVLANs) by searching corresponding DHCP snooping entries for DHCP client
information including IP addresses, MAC addresses, and CVLANs, before sending the packets to
clients. For details,
see
VLAN Mapping Configuration in the Layer 2 - LAN Switching
Configuration Guide
.
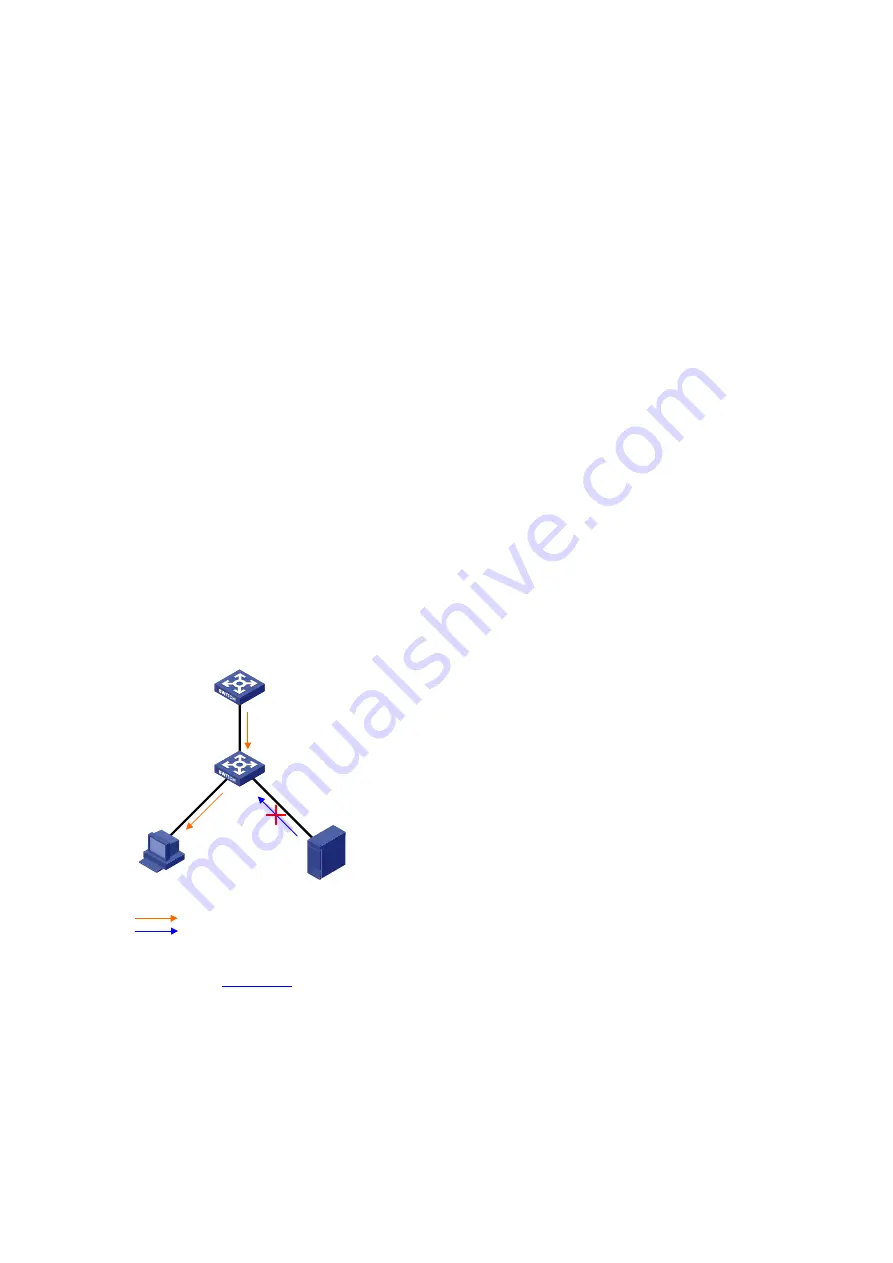
Application Environment of Trusted Ports
Configuring a trusted port connected to a DHCP server
Figure 9-1
Configure trusted and untrusted ports
Trusted
DHCP server
DHCP snooping
Untrusted
Untrusted
Unauthorized
DHCP server
DHCP client
DHCP reply messages
As shown in
, a DHCP snooping device’s port that is connected to an authorized DHCP
server should be configured as a trusted port to forward reply messages from the DHCP server, so
that the DHCP client can obtain an IP address from the authorized DHCP server.
Configuring trusted ports in a cascaded network
In a cascaded network involving multiple DHCP snooping devices, the ports connected to other DHCP
snooping devices should be configured as trusted ports.
To save system resources, you can disable the trusted ports, which are indirectly connected to DHCP
clients, from recording clients’ IP-to-MAC bindings upon receiving DHCP requests.
















































