9-8
DHCP Snooping Configuration Examples
DHCP Snooping Configuration Example
Network requirements
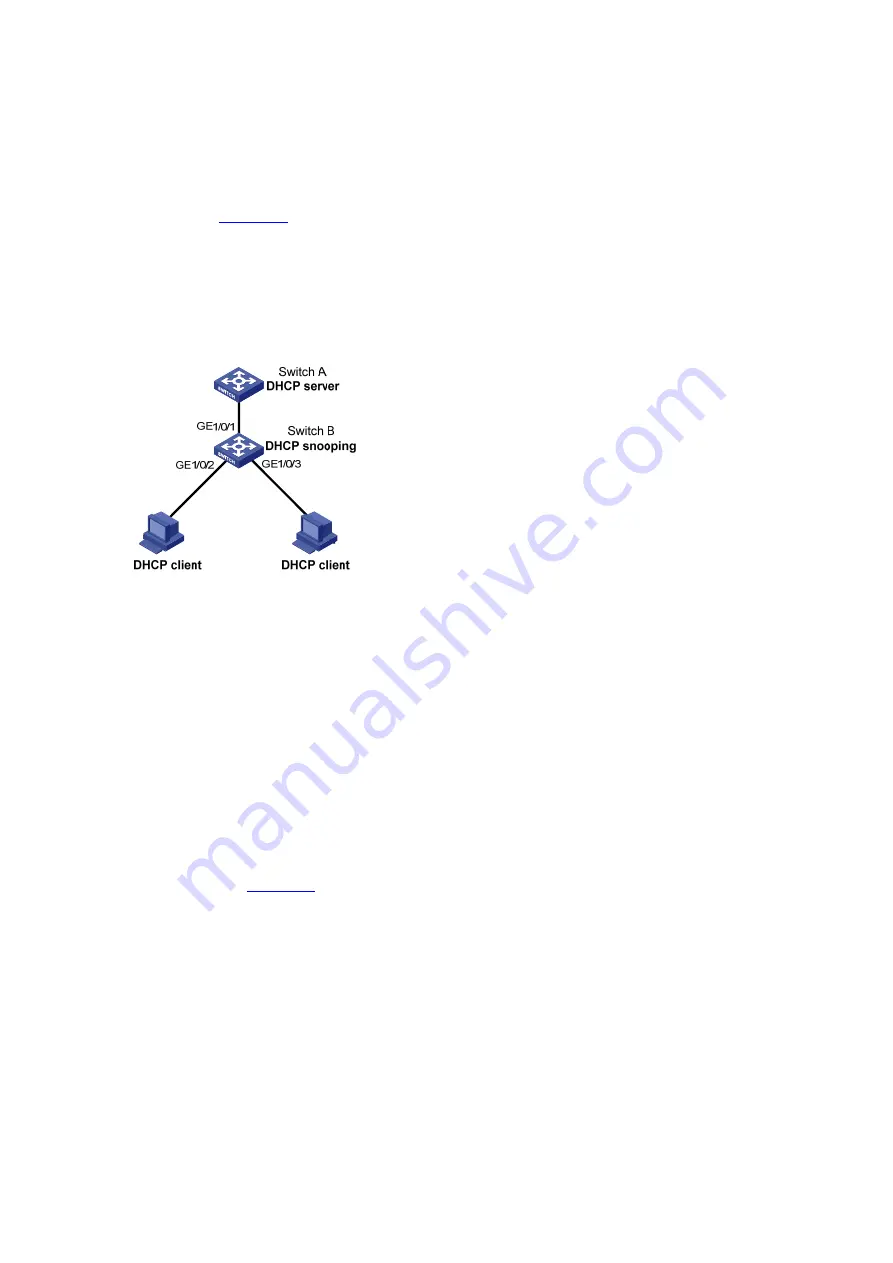
As shown in
, Switch B is connected to a DHCP server through GigabitEthernet 1/0/1, and
to two DHCP clients through GigabitEthernet 1/0/2 and GigabitEthernet 1/0/3. GigabitEthernet 1/0/1
forwards DHCP server responses while the other two do not.
Switch B records clients’ IP-to-MAC address bindings in DHCP-REQUEST messages and DHCP-ACK
messages received from trusted ports.
Figure 9-3
Network diagram for DHCP snooping configuration
Configuration procedure
# Enable DHCP snooping.
<SwitchB> system-view
[SwitchB] dhcp-snooping
# Specify GigabitEthernet 1/0/1 as trusted.
[SwitchB] interface GigabitEthernet 1/0/1
[SwitchB-GigabitEthernet1/0/1] dhcp-snooping trust
[SwitchB-GigabitEthernet1/0/1] quit
DHCP Snooping Option 82 Support Configuration Example
Network requirements
z
As shown in
, enable DHCP snooping and Option 82 support on Switch B.
z
Configure the handling strategy for DHCP requests containing Option 82 as
replace
.
z
On GigabitEthernet 1/0/2, configure the padding content for the circuit ID sub-option as
company001
and for the remote ID sub-option as
device001
.
z
On GigabitEthernet 1/0/3, configure the padding format as
verbose
, access node identifier as
sysname
, and code type as
ascii
for Option 82.
z
Switch B forwards DHCP requests to the DHCP server (Switch A) after replacing Option 82 in the
requests, so that the DHCP clients can obtain IP addresses.
Configuration procedure
# Enable DHCP snooping.
<SwitchB> system-view
















































