1-10
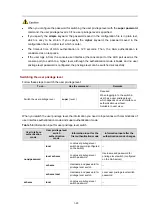
Table 1-4
Common command line errors
Error information
Cause
% Unrecognized command found at '^' position.
The command was not found.
% Incomplete command found at '^' position.
Incomplete command
% Ambiguous command found at '^' position.
Ambiguous command
Too many parameters
Too many parameters
% Wrong parameter found at '^' position.
Wrong parameters
Using Command History
The CLI automatically saves the commands recently used in the history command buffer. You can
access and execute them again.
Accessing History Commands
Follow a step below to access history commands:
To do…
Use the key/command…
Result
Display history commands
display history-command
Displays valid history commands you
used
Display the previous history
command
Up arrow key or
Ctrl+P
Displays the previous history command, if
any
Display the next history
command
Down arrow key or
Ctrl+N
Displays the next history command, if any
You can use arrow keys to access history commands in Windows 200X and XP Terminal or Telnet.
However, the up and down arrow keys are invalid in Windows 9X HyperTerminal, because they are
defined differently. You can press
Ctrl+P
or
Ctrl+N
instead.
z
The commands saved in the history command buffer are in the same format in which you typed the
commands. If you type an incomplete command, the command saved in the history command
buffer is also an incomplete one.
z
If you execute the same command repeatedly, the switch saves only the earliest record. However,
if you execute the same command in different formats, the system saves them as different
commands. For example, if you execute the
display cu
command repeatedly, the system saves
only one command in the history command buffer. If you execute the command in the format of
display cu
and
display current-configuration
respectively, the system saves them as two
commands.
z
By default, the CLI can save up to 10 commands for each user. To set the capacity of the history
command buffer for the current user interface, use the
history-command max-size
command.
Summary of Contents for SR6600 SPE-FWM
Page 112: ...6 101...