13-5
HTTPS Configuration Example
Network requirements
Users can access and control the device through logging in to the Web page. To prevent unauthorized
users from accessing and controlling the device and enhance the device management security, the
device requires the users log in to the Web page through HTTPS and authenticates the users using SSL,
and ensures that the transmitted data will not be spoofed and tampered.
To meet the requirements, perform the following configurations:
z
Configure
Device
as the HTTPS server and apply a certificate for
Device
.
z
Apply a certificate for the HTTPS client
Host
for
Device
to authenticate it.
The name of the CA (Certificate Authority) that issues certificate to Device is
new-ca
.
z
In this configuration example, Windows Server serves as CA and you need to install Simple
Certificate Enrollment Protocol (SCEP) component.
z
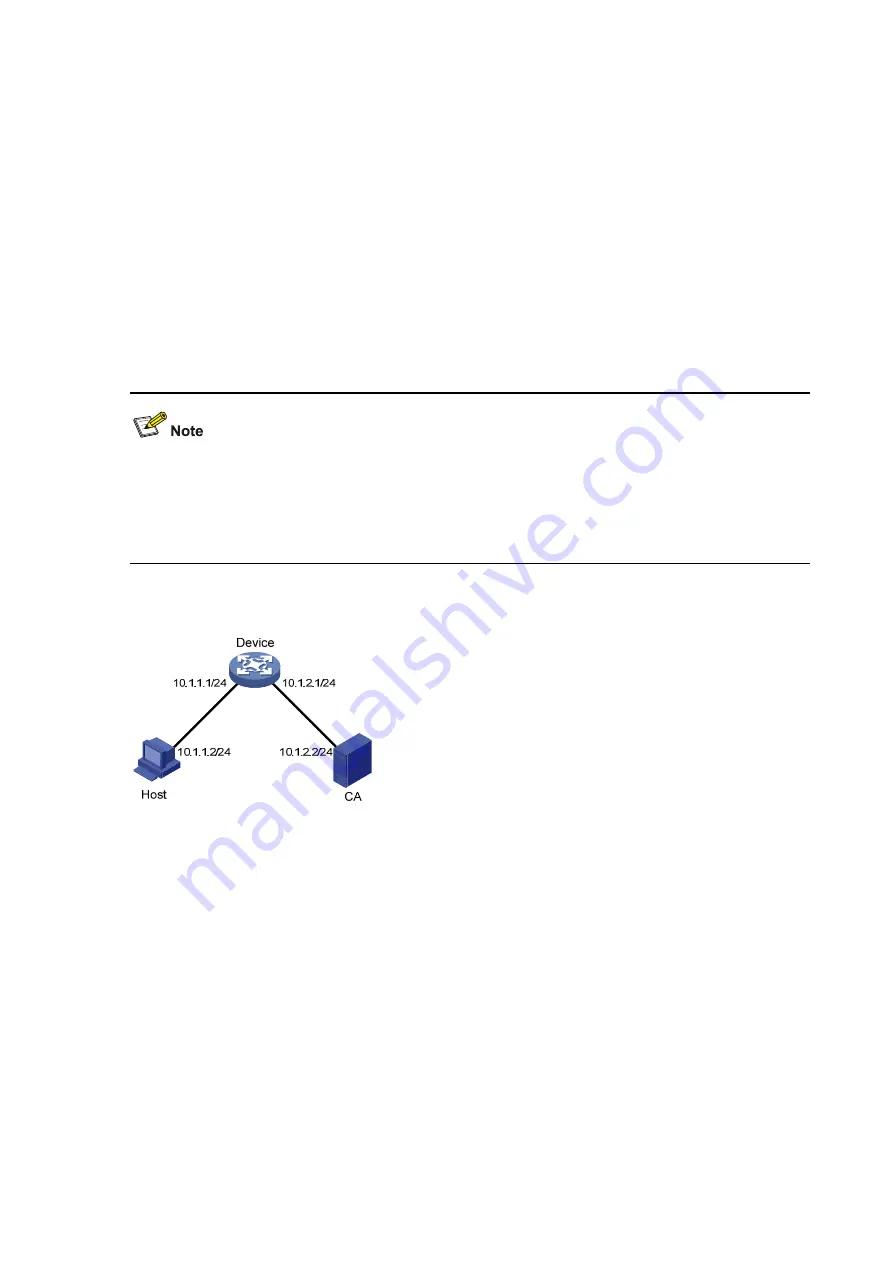
Before the following configurations, ensure that there is an available route between Device, Host
and CA.
Figure 13-1
Network diagram for HTTPS configuration
Configuration procedure
1) Configure the HTTPS server Device.
# Configure PKI entity
en
, and specify its common name as
http-server1
, and FQDN as
ssl.security.com
.
<Device> system-view
[Device] pki entity en
[Device-pki-entity-en] common-name http-server1
[Device-pki-entity-en] fqdn ssl.security.com
[Device-pki-entity-en] quit
# Configure PKI domain
1
, specify the trusted CA as
new-ca
, the URL of the server for certificate
request as
http://10.1.2.2/certsrv/mscep/mscep.dll
, the authority for certificate request as RA, and
the entity name as
en
.
[Device] pki domain 1
[Device-pki-domain-1] ca identifier new-ca
Summary of Contents for WA Series
Page 10: ...v 15 Index 15 1...