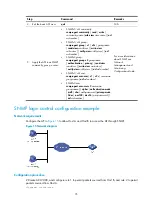
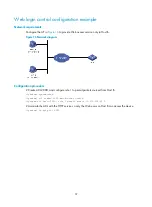
32
Controlling user logins
To harden device security, use ACLs to prevent unauthorized logins. For more information about ACLs,
see
ACL and QoS Configuration Guide.
Controlling Telnet logins
Use a basic ACL (2000 to 2999) to filter Telnet traffic by source IP address. Use an advanced ACL (3000
to 3999) to filter Telnet traffic by source and/or destination IP address. Use an Ethernet frame header
ACL (4000 to 4999) to filter Telnet traffic by source MAC address.
To access the device, a Telnet user must match a permit statement in the ACL applied to the user interface.
Configuring source IP-based Telnet login control
Step Command Remarks
1.
Enter system view.
system-view
N/A
2.
Create a basic ACL and enter
its view, or enter the view of an
existing basic ACL.
acl
[
ipv6
]
number
acl-number
[
name
name
] [
match-order
{
config
|
auto
} ]
By default, no basic ACL
exists.
3.
Configure an ACL rule.
•
For IPv4 networks:
rule
[
rule-id
] {
deny
|
permit
}
[
counting
|
fragment
|
logging
|
source
{
sour-addr sour-wildcard
|
any
} |
time-range
time-range-name
]
*
•
For IPv6 networks:
rule
[
rule-id
] {
deny
|
permit
}
[
counting
|
fragment
|
logging
|
routing
[
type
routing-type
]
|
source
{
ipv6-address
prefix-length
|
ipv6-address
/
prefix-length
|
any
} |
time-range
time-range-name
]
By default, a basic ACL
does not contain any rule.
4.
Exit the basic ACL view.
quit
N/A
5.
Enter user interface view.
user-interface
[
type
]
first-number
[
last-number
]
N/A
6.
Use the ACL to control user
logins by source IP address.
acl
[
ipv6
]
acl-number
{
inbound
|
outbound
}
•
inbound
: Filters
incoming packets.
•
outbound
: Filters
outgoing packets.
Configuring source/destination IP-based Telnet login control