Appendix A: Text Formatting
110
Modero G4 Touch Panels - Configuration & Programming Manual
Input mask literals
To define a literal character, enter any character, other than those shown in the above table
(including spaces, and symbols)
. A
back-slash ('\') causes the character that follows it to be displayed as the literal character. For example,
\A
is displayed just as the
letter
A
. To define one of the following characters as a literal character, precede that character with a back-slash. Text entry
operation using Input Masks.
A keyboard entry using normal text entry is straightforward. However, once an input mask is applied, the behavior of the keyboard
needs to change to accommodate the input mask's requirement. When working with masks, any literal characters in the mask will
be "skipped" by any cursor movement, including cursor, backspace, and delete keys.
When operating with a mask, the mask should be displayed with placeholders. The "-" character should display where you should
enter a character. The arrow keys will move between the "-" characters and allow you to replace them. The text entry code operates
as if it is in the overwrite mode. If the cursor is positioned on a character already entered and you type in a new (and valid)
character, the new character replaces the old character. There is no shifting of characters.
When working with ranges specified by the [] mask, the keyboard allows you to enter a number between the values listed in the
ranges. If a user enters a value that is larger than the maximum, the maximum number of right-most characters is used to create a
new, acceptable value.
Example 1
: If you type "125" into a field accepting 0-100, then the values displayed will be "1", "12", "25".
Example 2
: If the max for the field was 20, then the values displayed will be "1", "12", "5".
When data overflows from a numerical field, the overflow value is added to the previous field on the chain if the overflow character
was specified. In the above example, if the overflow flag was set, the first example will place the "1" into the previous logical field
and the second example will place "12" in the previous logical field.
If the overflow field already contains a value, the new value will be inserted to the right of the current characters and the overflow
field will be evaluated. Overflow continues to work until a field with no overflow value is set or no more fields remain (i.e. reached
first field).
If a character is typed and that character appears in the Next Field list, the keyboard should move the focus to the next field. For
example, when entering time, a
":"
is used as a next field character. If you enter "1:2", the 1 is entered in the current field (hours)
and then the focus is moved to the next field and 2 is entered in that field.
When entering time in a 12-hour format, entry of AM and PM is required. Instead of adding AM/PM to the input mask specification,
the AM/PM should be handled within the NetLinx code. This allows a programmer to show/hide and provide discrete feedback for
AM and PM.
Input mask output examples
The following are some common input masking examples:
URL Resources
A URL can be broken into several parts. For example, with the URL
http://www.amx.com/company-info-home.asp
, this URL
indicates that the protocol in use is
http
(HyperText Transport Protocol) and that the information resides on a host machine named
www.amx.com
. The image on that host machine is given an assignment (
by the program
) name of
company-info-home.asp
(Active
Server Page)
.
The exact meaning of this name on the host machine is both protocol dependent and host dependent. The information normally
resides in a file, but it could be generated dynamically. This component of the URL is called the file component, even though the
information is not necessarily in a file.
A URL can optionally specify a port, which is the port number to which the TCP/IP connection is made on the remote host machine.
If the port is not specified, the default port for the protocol is used instead. For example, the default port for http is
80
. An
alternative port could be specified as:
http://www.amx.com:8080/company-info-home.asp
.
NOTE:
Any legal HTTP syntax can be used.
Special Escape Sequences
The system has only a limited knowledge of URL formats, as it transparently passes the URL information onto the server for
translation. A user can then pass any parameters to the server side programs such as CGI scripts or active server pages. However;
the system will parse the URL looking for special escape codes. When it finds an escape code, it replaces that code with a particular
piece of panel, button, or state information.
For example, "http://www.amx.com/img.asp?device=$DV" would become
http://www.amx.com/img.asp?device=10001
.
Other used escape sequences include:
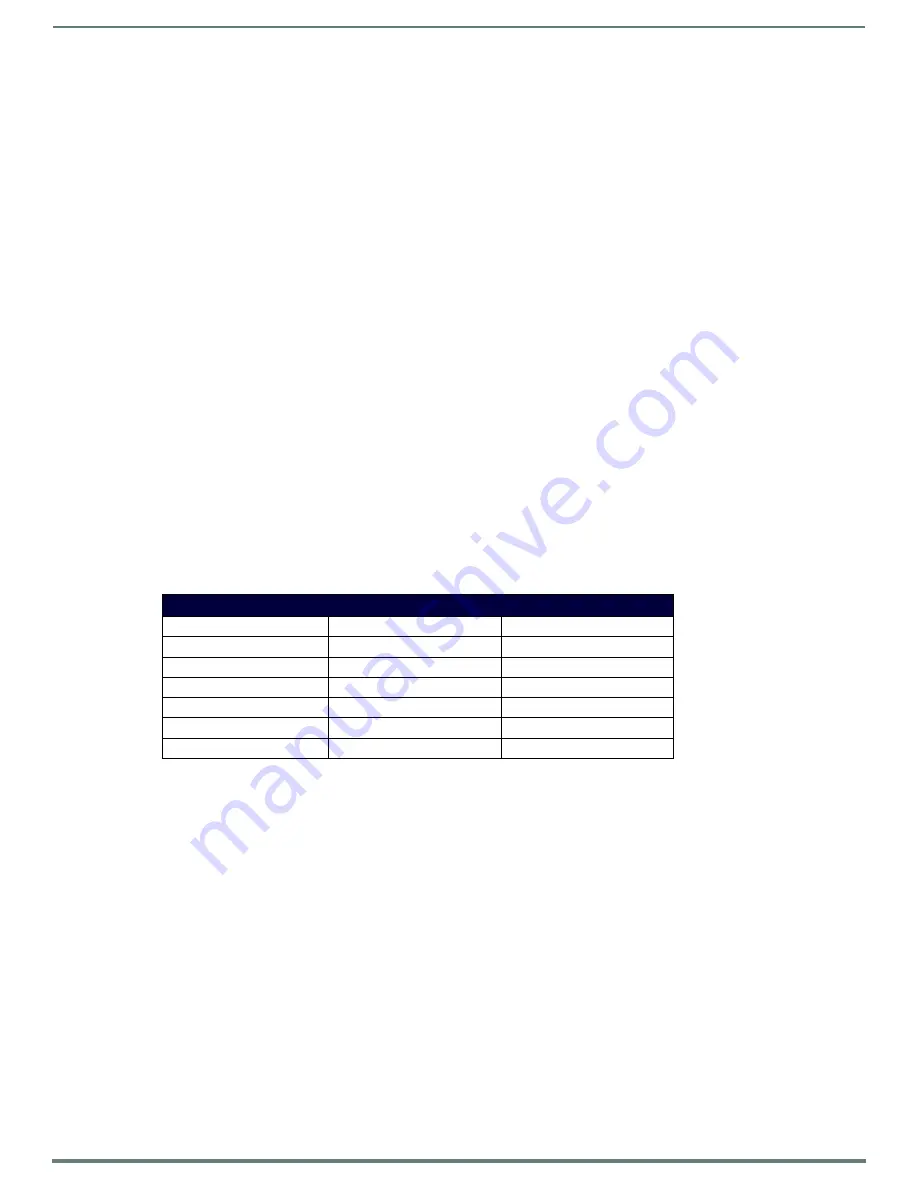
Output Examples
Common Name
Input Mask
Input
IP Address Quad
[0|255]{.}
Any value from 0 to 255
Hour
[1|12]{:}
Any value from 1 to 12
Minute/Second
[0|59]{:}
Any value from 0 to 59
Frames
[0|29]{:}
Any value from 0 to 29
Phone Numbers
(999) 000-0000
(555) 555-5555
Zip Code
00000-9999
75082-4567