Public Key Infrastructure
229/263
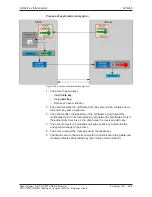
client verifies the signature of the certificate using trustworthy root
certificates which the Edge Gateway has stored in its local directory of
trustworthy certificates. Only if the verification results in a valid authenticity,
the Edge Gateway uses the received key.
When the Edge Gateway is delivered, it already has a directory with
trustworthy certificates (Trusted Certification Authorities). You can add
more trustworthy certificates or delete them. The preinstalled certificates
are from the Mozilla CA Store (
https://www.mozilla.org/en-US/about/
governance/policies/security-group/certs/
, e.g. List of included root
certificates).
Figure 146: Use case 1: Verification of the authenticity of the communication partner
(Server)
A trustworthy certificate can require another trustworthy certificate to verify
authenticity. A so called
Hierarchy of trust
[
}
page 227] results from this.
Needed for verification, the Edge Gateway requires all trustworthy
certificates of a specific server certificate. For this, if applicable, you have to
load more trustworthy certificates into the directory of trustworthy
certificates (Trusted Certification Authorities) of the Edge Gateway.
For details about “How to work with the certificates of this list (Upload,
Download, Removal, Creation, Show List)”, see section
Working with root
certificates
[
}
page 234].
Edge Gateway | NIOT-E-TIB100-GB-RE (Remote)
DOC170501UM04EN | Revision 4 | English | 2018-08 | Released | Public
© Hilscher 2017 – 2018