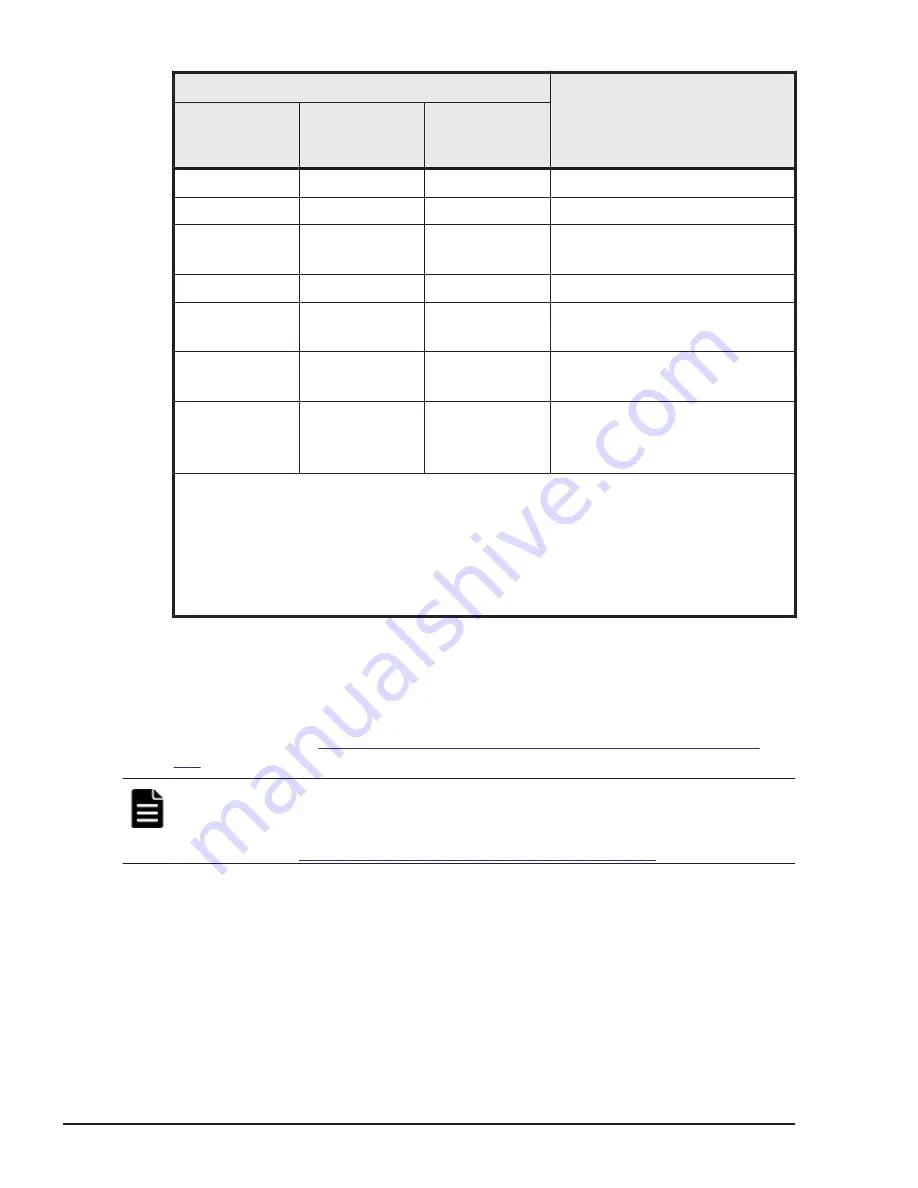
Command device setting
Security to be set
Security
User
authentication
Group
information
acquisition
0
0
1
Only HORCM_DEV allowed
0
1
0
User authentication required
0
1
1
User authentication required
Only HORCM_DEV allowed
1
0
0
CMD security
1
0
1
CMD security
Only HORCM_DEV allowed
1
1
0
CMD security
User authentication required
1
1
1
CMD security
User authentication required
Only HORCM_DEV allowed
Notes:
•
Only HORCM_DEV allowed: means to be able to perform the operation for only
paired logical volumes described at HORCM_DEV.
•
User authentication required: means that only the commands issued by the
authorized users can be executed.
•
CMD security: means that only the devices recognizable from the host can be
operated.
The Data Protection Facility uses an enhanced command device that you
define using the LUN Manager software (or SNMP). When you define the
command device, the DataProtection Facility is turned ON or OFF to each
command device, which has an attributes to enable the Data Protection
Facility. CCI distinguishes the ON from OFF attribute when CCI recognizes the
Figure 7-1 Definition of the protection volumes on page
shows the definition of protected volumes.
Note:
If the command device is set to enable protection mode, there is no
impact on CCI operations. CCI controls pairs under current specification. For
details about the command operations when the Data Protection Facility is
Target commands for protection on page 7-9
.
7-6
Data protection operations with CCI
Command Control Interface User and Reference Guide
Summary of Contents for HUS VM
Page 10: ...x Command Control Interface User and Reference Guide ...
Page 18: ...xviii Preface Command Control Interface User and Reference Guide ...
Page 78: ...2 50 CCI software environment Command Control Interface User and Reference Guide ...
Page 154: ...4 8 Starting up CCI Command Control Interface User and Reference Guide ...
Page 191: ...Provisioning operations with CCI 5 37 Command Control Interface User and Reference Guide ...
Page 280: ...6 56 Data replication operations with CCI Command Control Interface User and Reference Guide ...
Page 286: ...6 62 Data replication operations with CCI Command Control Interface User and Reference Guide ...
Page 302: ...7 16 Data protection operations with CCI Command Control Interface User and Reference Guide ...
Page 324: ...8 22 Examples of using CCI commands Command Control Interface User and Reference Guide ...
Page 524: ...9 200 Troubleshooting Command Control Interface User and Reference Guide ...
Page 529: ...Command Control Interface User and Reference Guide ...
















































