ADMIN
Version 1.0, 02/2015. Copyright 2012 Hitron Technologies
95
Version 1.0, 02/2015. Copyright 2014 Hitron Technologies
95
Hitron CGNVM User’s Guide
Traceroute: this tool allows you to see the route taken by data packets to get
from the CGNVM to the destination you specify. You can use this tool to solve
routing problems, or identify firewalls that may be blocking your access to a
computer or service.
5.2
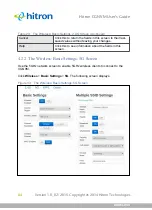
The Admin: Management Screen
Use this screen to make changes to the CGNVM’s login credentials (username and
password) and inactivity idle time.
NOTE:
If you forget your password, you will need to reset the CGNVM to its factory
defaults.
Click
Admin
>
Management
. The following screen displays.
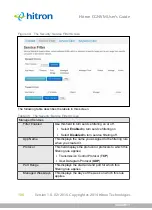
Figure 37:
The Admin: Management Screen
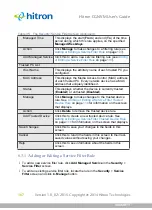
The following table describes the labels in this screen.
Table 28:
The Admin: Management Screen
Username
If your CGNVM supports multiple user accounts, select
the account you want to modify from the list.
Old Password
Enter the password with which you currently log into the
CGNVM for this account.