Version 1.0, 11/2016. Copyright 2012 Hitron Technologies
85
Version 1.0, 11/2016. Copyright 2016 Hitron Technologies
85
Hitron CODA-4x8x User’s Guide
5.1.5
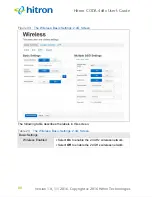
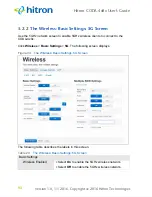
Service Sets and SSIDs
Each wireless network, including all the devices that comprise it, is known as a
Service Set.
NOTE:
Depending on its capabilities and configuration, a single wireless access
point may control multiple Service Sets; this is often done to provide different
service or security levels to different clients.
Each Service Set is identified by a Service Set IDentifier (SSID). This is the name of
the network. Wireless clients must know the SSID in order to be able to connect to
the AP. You can configure the CODA-4x8x to broadcast the SSID (in which case, any
client who scans the airwaves can discover the SSID), or to “hide” the SSID (in which
case it is not broadcast, and only users who already know the SSID can connect).
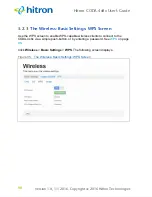
5.1.6
Wireless Security
Radio is inherently an insecure medium, since it can be intercepted by anybody in the
coverage area with a radio receiver. Therefore, a variety of techniques exist to control
authentication (identifying who should be allowed to join the network) and encryption
(signal scrambling so that only authenticated users can decode the transmitted data).
The sophistication of each security method varies, as does its effectiveness. The
CODA-4x8x supports the following wireless security protocols (in order of
effectiveness):
WPA-PSK
(WiFi Protected Access - Pre-Shared Key): WPA was created to
solve the inadequacies of WEP, the Wired Equivalency Protocol, which is now
considered obsolete. There are two types of WPA: the “enterprise” version
(known simply as WPA) requires the use of a central authentication database
server, whereas the “personal” version (supported by the CODA-4x8x) allows
users to authenticate using a “pre-shared key” or password instead. While WPA
provides good security, it is still vulnerable to “brute force” password-guessing
attempts (in which an attacker simply barrages the AP with join requests using
different passwords), so for optimal security it is advised that you use a random
password of thirteen characters or more, containing no “dictionary” words.
WPA2-PSK
: WPA2 is an improvement on WPA. The primary difference is that
WPA uses the Temporal Key Integrity Protocol (TKIP) encryption standard
(which has been shown to have certain possible weaknesses), whereas WPA2
uses the stronger Advanced Encryption Standard (AES) in the Counter mode
with Cipher block chaining Message authentication code Protocol (CCMP),