23
4.
, ACS and IDS
(reader with keypad)
Introduction to operating sequences
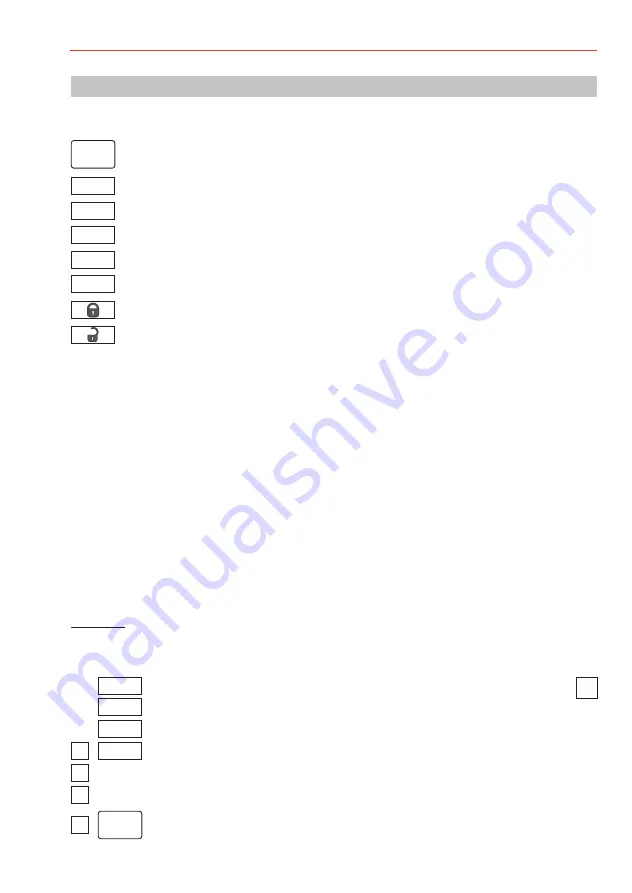
The following symbols are used to represent an operating step:
possible
X
F
0....9
3
0....9
and
or
ID
X
X
X
ID
0....9
i
F
3
r
Hold the mifare ID data carrier in the reading field
Entry using number buttons
Info button
Function button
Confirm entry, OK
Delete entry, cancel action
Arm intrusion detection system
Disarm intrusion detection system
The sequence of operation as well as the possible scope of functions for the reader depends on the
controller used and how it is programmed. The programming of the system defines, among other
things, the authorization procedure. The authorization procedure defines which identifying
characteristics are required to perform an action. Various actions (such as access control and control
functions) can have different authorization procedures.
Possible authorization procedures are:
- PIN only (PIN = personal identification number)
- Data carrier only
- PIN or data carrier
- PIN and data carrier
With use in access control systems, the use of door codes instead of PINs is possible if this function
is supported by the superordinate system.
Mark the actual settings of your system in the instructions below so that you always know which
functions are possible and what authorization procedure applies to the relevant function. Your
installer can help you with this.
Activate control function/macro with PIN or data carrier
(marking not necessary for mandatory operating steps)
Example:
Press the “F” button.
Enter the function number (macro number)
Confirm with the “OK” button.
Enter PIN
Hold the data carrier in the reading field
Operating Instructions mifare/DESFire EV1 reader "Accentic" with/without keypad














































