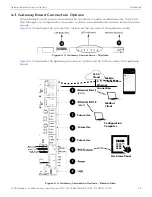
CLSS Gateway - Installation and Users’ Manual | P/N:LS10248-000HW-E | REV. F | FEB/11/2022
19
Section 3: Security
Recommendations
3.1 For Users
An administrator should:
•
Regularly review the user roles and permissions for a CLSS account
•
Immediately remove users who should no longer have access to CLSS
A technician should:
•
Use discretion to allow or deny a location access request.
•
Disconnect the
CLSS App
from the
CLSS Gateway
, once the required activity is
completed.
•
Turn OFF the location access in the CLSS App's
Security Settings
, when location
access is not required.
3.2 For Preventing Potential Risks
Security threats applicable to networked systems include unauthorized access,
communication snooping, viruses, and other malicious software agents.
3.2.1 Unauthorized Access
Unauthorized access results from unsecured user name and password, uncontrolled
access to the equipment, or uncontrolled and unsecured access to the network.
It results the following:
•
Loss of system availability
•
Incorrect execution of controls causing damage to the equipment
•
Incorrect operation, spurious alarms, or both
•
Theft or damage to the contents of the system
•
Capture and modification or deletion of data causing possible liability to the
installation Site and Honeywell
User Access and Passwords
Observe the following good practices:
•
The password has one numerical, one upper case, one lower case, and one special
character whenever any user registers or changes the credentials.
•
Enforce a password change periodically
•
Do now allow any dictionary words as passwords
•
Check passwords against known common weak password databases
•
Do not allow common and predictable passwords though they meet other
requirements. For example: P@SSw0rd
•
Not allow usernames, service names, or any such context-specific words
•
Passwords should be complex and not easily guessed; and, should not contain
phrases used in common speech.
•
Do not use personally identifiable information as a password, such as social security
numbers, addresses, birth dates.
•
Provide only the minimum level of access and privileges for each user.
•
Ensure physical security of passwords. Avoid and warn against writing user names
and passwords where they can be seen by unauthorized personnel.
•
Periodically audit user accounts and remove any that are no longer required.
3.2.2 Memory Media
•
Use only authorized removable media.
•
Use an up-to-date anti-virus software to scan the removable media and check for
viruses and malware.
•
Ensure that the memory media is not used for other purposes to avoid risk of
infection.
•
Control access to media containing backups to avoid risk of tampering.