358
DCFM Professional User Manual
53-1001773-01
Steps for connecting to an LKM appliance
14
Exporting and registering the switch KAC certificates on LKM
The encryption switch self-signed KAC certificates must exported and then registered on the LKM
appliance.
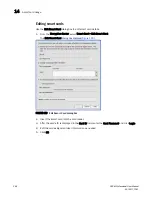
1. From the Encryption Center, select Switch > Export Certificate.
The Export Switch Certificate dialog box displays.
2. Select Self-signed switch certificate (X.509) and click OK.
A dialog box displays that allows you to save the CSR to your SAN Management Program client
PC, or an external host of your choosing.
3. Register the self-signed KAC certificate you exported from the member node with the NetApp
LKM appliance.
LKM key vault high availability deployment
LKM appliances can be clustered together to provide high availability capabilities. You can deploy
and register one LKM with an encryption switch or blade and later deploy and register another LKM
at any time, if LKMs are clustered or linked together. Please refer to LKM documentation to link or
cluster the LKMs.
When LKM appliances are clustered, both LKMs in the cluster must be registered and configured
with the link keys before starting any crypto operations. If two LKM key vaults are configured, they
must be clustered. If only a single LKM key vault is configured, it may be clustered for backup
purposes, but it will not be directly used by the switch.
When dual LKMs are used with the encryption switch or blade, the dual LKMs must be clustered.
There is no enforcement done at the encryption switch or blade to verify whether or not the dual
LKMs are clustered, but key creation operations will fail if you register non-clustered dual LKMs
with the encryption switch or blade.
Regardless of whether you deploy a single LKM or clustered dual LKMs, register only the primary
key vault with the encryption switch or blade. You do not need to register a secondary key vault.
Disk keys and tape pool keys (Brocade native mode support)
DEK creation, retrieval, and update for disk and tape pool keys in Brocade native more are as
follows:
•
DEK creation - The DEK is archived into the primary LKM. Upon successful archive of DEK onto
primary LKM, the DEK is read from secondary LKM until it is synchronized to the secondary
LKM, or a timeout of 10 seconds occurs (2 seconds with 5 retries). If successful, then the DEK
created can be used for encrypting disk LUNs or tape pool in Brocade native mode. If key
archival of the DEK to primary LKM fails, an error is logged and the operation is retried. If the
failure happens after archival of the DEK to the primary LKM, but before synchronization to the
secondary, a VAULT_OFFLINE error is logged and the operation is retried. Any DEK archived to
the primary in this case is not used.
•
DEK retrieval - The DEK is retrieved from the primary LKM if the primary LKM is online and
reachable. If the registered primary LKM is not online or not reachable, the DEK is retrieved
from a clustered secondary LKM.
•
DEK Update - DEK Update behavior is same as DEK Creation.
Summary of Contents for Brocade BladeSystem 4/12
Page 1: ...53 1001773 01 14 April 2010 DCFM Professional User Manual Supporting DCFM 10 4 X ...
Page 3: ...DCFM Professional User Manual iii 53 1001773 01 ...
Page 4: ...iv DCFM Professional User Manual 53 1001773 01 ...
Page 88: ...56 DCFM Professional User Manual 53 1001773 01 Seed switch 2 ...
Page 146: ...114 DCFM Professional User Manual 53 1001773 01 Customizing the main window 4 ...
Page 152: ...120 DCFM Professional User Manual 53 1001773 01 Launching HCM Agent 5 ...
Page 246: ...214 DCFM Professional User Manual 53 1001773 01 Syslog forwarding 8 ...
Page 262: ...230 DCFM Professional User Manual 53 1001773 01 Generating zoning reports 10 ...
Page 662: ...630 DCFM Professional User Manual 53 1001773 01 ...