DCFM Professional User Manual
401
53-1001773-01
Configuring hosts for encryption targets
14
Configuring hosts for encryption targets
Use the Encryption Target Hosts dialog box to edit (add or remove) hosts for an encrypted target.
NOTE
Hosts are normally selected as part of the Configure Storage Encryption wizard but you can also edit
hosts later using the Encryption Target Hosts dialog box.
1. Select Configure > Encryption from the menu bar.
The Encryption Center dialog box displays.
2. Select the encryption group, switch, or encryption engine containing the storage device to be
configured.Right-click, or select Group, Switch, or Engine from the menu bar.
3. Select Targets.
The Encryption Targets dialog box displays.
4. Select a Target storage device from the list, and click Hosts.
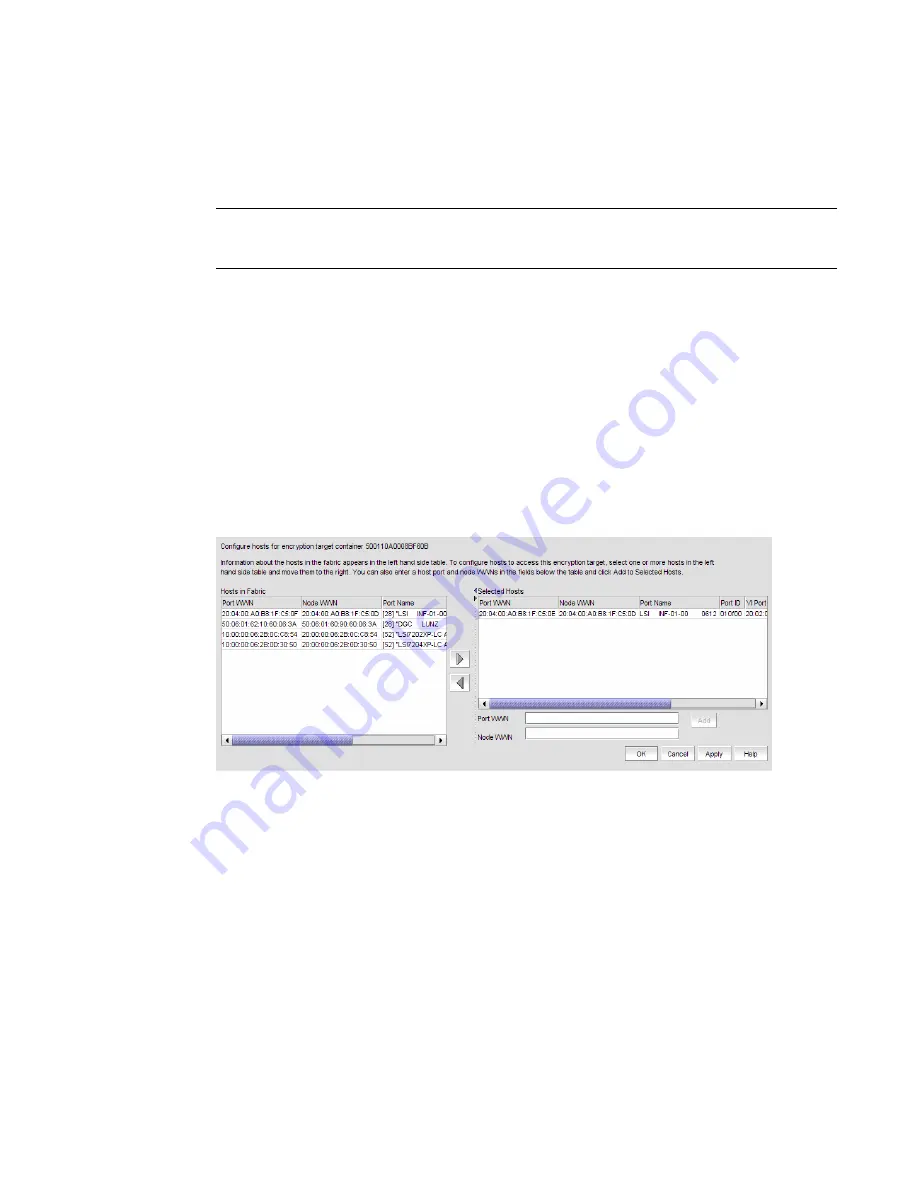
The Encryption Target Hosts dialog box displays. This dialog box lists configured hosts in a
fabric.
5. Select one or more hosts in a fabric and move them to the Selected Hosts table.
FIGURE 163
Encryption Target Hosts dialog box
Summary of Contents for Brocade BladeSystem 4/12
Page 1: ...53 1001773 01 14 April 2010 DCFM Professional User Manual Supporting DCFM 10 4 X ...
Page 3: ...DCFM Professional User Manual iii 53 1001773 01 ...
Page 4: ...iv DCFM Professional User Manual 53 1001773 01 ...
Page 88: ...56 DCFM Professional User Manual 53 1001773 01 Seed switch 2 ...
Page 146: ...114 DCFM Professional User Manual 53 1001773 01 Customizing the main window 4 ...
Page 152: ...120 DCFM Professional User Manual 53 1001773 01 Launching HCM Agent 5 ...
Page 246: ...214 DCFM Professional User Manual 53 1001773 01 Syslog forwarding 8 ...
Page 262: ...230 DCFM Professional User Manual 53 1001773 01 Generating zoning reports 10 ...
Page 662: ...630 DCFM Professional User Manual 53 1001773 01 ...