108
place by using shell scripts, such as the IPSec filters, to secure the MSBP for each of the security
environments defined in this guide.
2.8.7.1
Manually Adding Unique Security Groups to User Rights Assignments
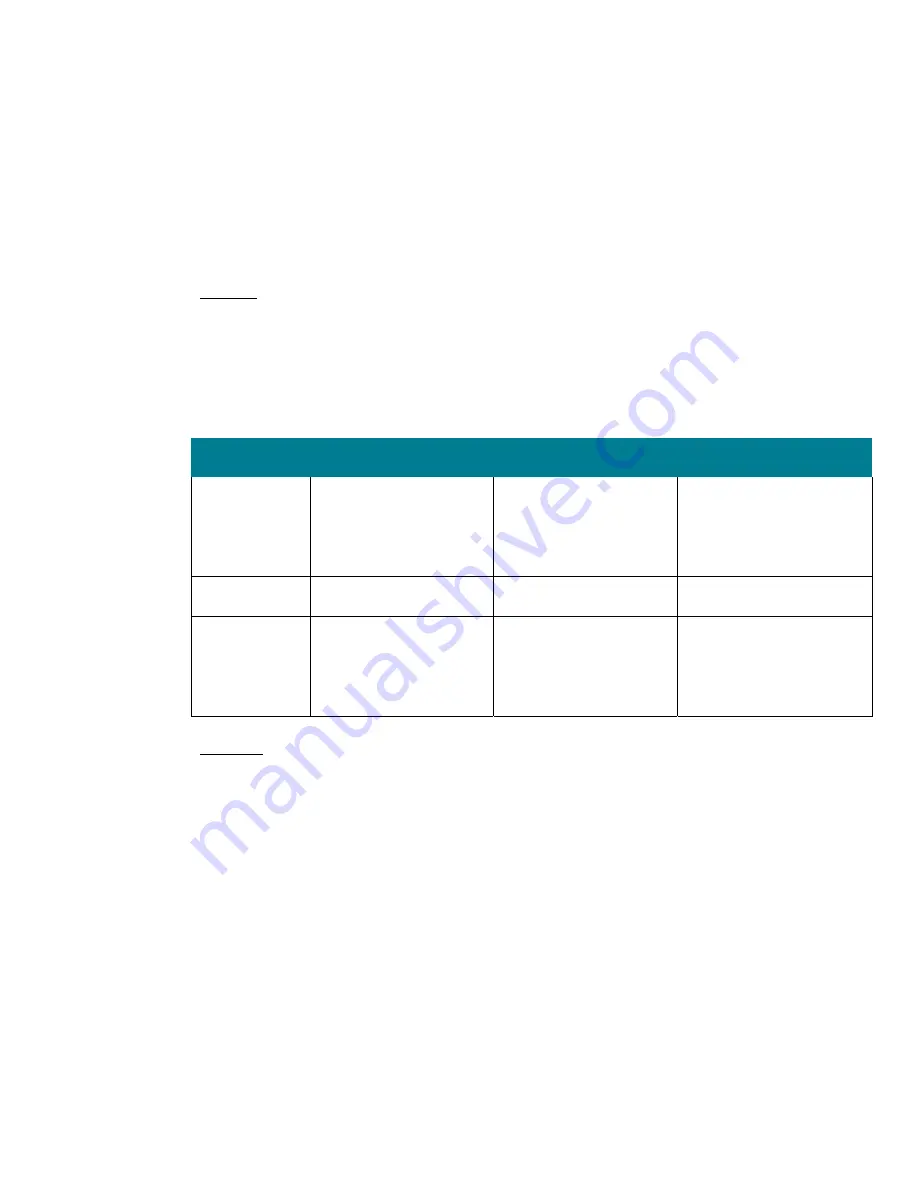
Most of the recommended security groups for User Rights Assignments have been configured within
the security templates that accompany this guide. However, there are a few rights that cannot be
included in the security templates, because the SIDs of the certain security groups are unique between
different Windows 2003 domains. The problem is that the unique RID (Relative Identifier), which is
part of the SID, is unique. These unique instances are described in the table below.
Warning:
The table below contains values for Built-in Administrator. The Built-in Administrator is the
built-in user account, not the security group "Administrators". If the security group Administrators is
added to any of the deny access user rights below, administrators will need to log on locally in order
to correct the mistake of adding the Administrators group to these rights. In addition, the Built-in
Administrator account may have a new name from renaming the Administrator account based on the
recommendations from above. When adding this account, remember to select the newly renamed
administrator account.
Setting Name
in UI
Legacy Client
Enterprise Client
High Security
Deny access to
this computer
from the
network
Built-in Administrator;
Support_388945a0;
Guest; all NONOperating
System service accounts
Built-in Administrator;
Support_388945a0;
Guest; all NONOperating
System service accounts
Built-in Administrator;
Support_388945a0;
Guest; all NONOperating
System service accounts
Deny log on as
a batch Job
Support_388945a0
and Guest
Support_388945a0
and Guest
Support_388945a0
and Guest
Deny log on
through
Terminal
Services
Built-in Administrator;
Support_388945a0;
Guest; Guests all
NONOperating System
service accounts
Built-in Administrator;
Support_388945a0;
Guest; Guests all
NONOperating System
service accounts
Built-in Administrator;
Support_388945a0;
Guest; Guests all
NONOperating System
service accounts
Important:
All NON-operating system service accounts are service accounts for specific applications
in the enterprise network. This does
not
include LOCAL SYSTEM, LOCAL SERVICE, or the NETWORK
SERVICE accounts that are built-in accounts for the operating system.
To manually add the above security groups to the Member Server Baseline Policy, follow the steps
below:
To add security groups to the User Rights Assignments:
1.
In Active Directory Users and Computers, right-click the
Member
Servers
OU, and then select
Properties.
2.
On the
Group
Policy
tab, select the
Enterprise Client Member Server Baseline Policy
to edit the
linked GPO.
3.
Select
Enterprise Client-Member Server Baseline Policy
, and then click
Edit
.
4.
In the Group Policy window, click
Computer Configuration\Windows Settings\Security
Setting\Local Policies\User Rights Assignment
to add the unique security groups from the table
above for each right.
5.
Close the Group Policy that has been modified.
6.
Close the
Member Servers
OU Properties window.