113
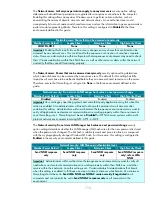
Deny log on through Terminal Services
Member Server Default
Legacy Client
Enterprise Client
High Security Client
Not Defined
Built-in Administrator;
Guests;
Support_388945a0;
Guest ;all NON-
operating system
service accounts
Built-in Administrator;
Guests;
Support_388945a0;
Guest ;all NON-
operating system
service accounts
Built-in Administrator;
Guests;
Support_388945a0;
Guest ;all NON-
operating system
service accounts
Important:
For all HP NAS server systems, administrators should only deny Guests,
Support_388945a0, Guest, and all NON-operating system service accounts
Note:
ANONOYMOUS LOGON, Built-in Administrator, Support_388945a0; Guest; and all NON-
operating system service accounts are not included in the .inf security template. These accounts and
groups have unique SIDs for each domain in the network. Therefore, they must be added manually.
For further information, see the Manual Hardening Procedures in section 2.8.7.
The
Deny log on through Terminal Services
user right determines which users and groups are
prohibited from logging on as a Terminal Services client. After joining the baseline member server to
a domain environment, there is no need to use local accounts to access the server from the network.
Domain accounts can access the server for administration and end-user processing. Remember, the
MSBP will not receive this Group Policy until the server is joined to the domain and restarted twice.
Therefore, the use of the local Administrator accounts is prohibited.
2.9.3
Security Options
Most Security Options for file servers in the three environments defined in this guide are configured
via the MSBP. For more information on the MSBP, see section 2.8. Differences between the MSBP
and the Incremental file server Group Policy are described in the following section.
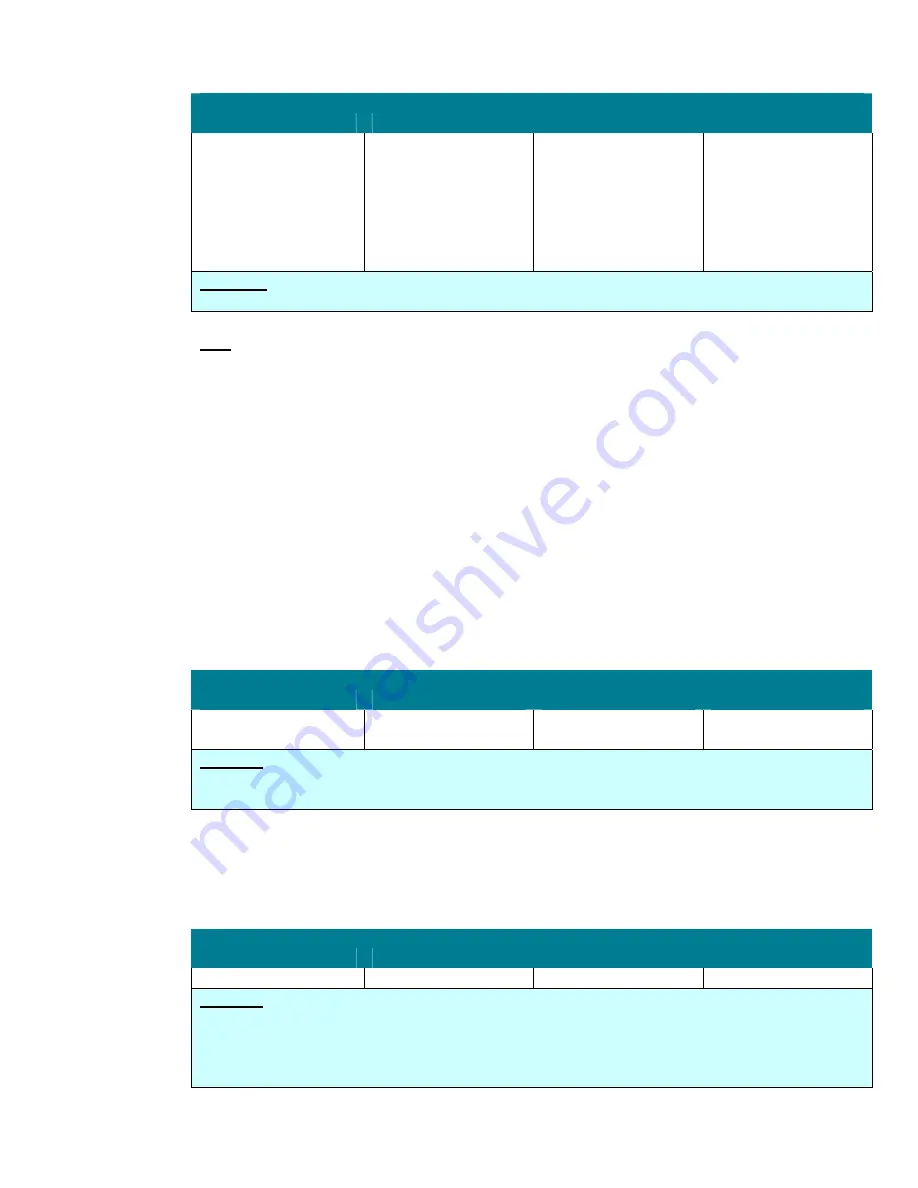
Accounts: Guest account status
Member Server Default
Legacy Client
Enterprise Client
High Security Client
Disabled
Disabled
Disabled
Disabled
Important:
Administrators need to check if any of their 3
rd
party applications use and require the
Guest account for communication or functionality purpose. If so, administrators may need to set this
security policy to
Enabled.
The
A
ccounts: Guest account status
security option setting determines whether the Guest account is
enabled or disabled. This account allows unauthenticated network users to gain access to the system
by logging in as
Guest
. Therefore, this security option setting is configured to
Disabled
in all three
environments.
Domain member: Digitally encrypt or sign secure channel data (always)
Member Server Default
Legacy Client
Enterprise Client
High Security Client
Enabled Disabled Disabled Enabled
Important:
In order to take advantage of this security option setting on member workstations and
servers, all domain controllers that constitute the member’s domain must be running Windows NT 4.0
with Service Pack 6a or later; this is not supported in Windows 98 Second Edition clients (unless they
have the dsclient installed). This setting must be set to
Disabled
for HP NAS server systems within
multi-protocol network environments involving NFS, AFTP, or NCP.