31
could make it impossible for users to log on to the domain or to get authorization for accessing
domain resources after logging on.
Debug Programs
Member Server Default
Legacy Client
Enterprise Client
High Security Client
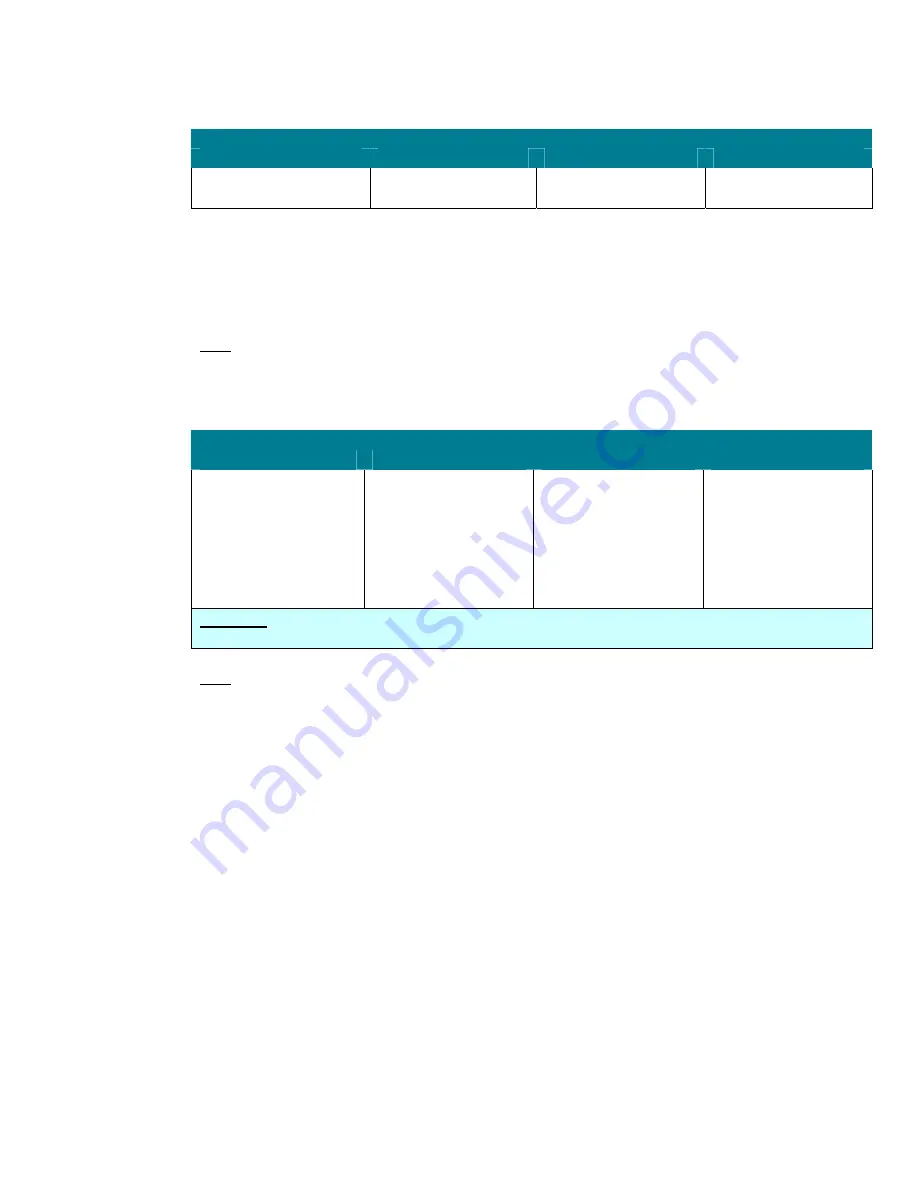
Administrators
Revoke all security
groups and accounts
Revoke all security
groups and accounts
Revoke all security
groups and accounts
The
Debug programs
user right determines which users can attach a debugger to any process or to
the kernel. This user right provides complete access to sensitive and critical operating system
components. Program debugging should not take place in production environments except in extreme
circumstances, such as troubleshooting a business-critical application that cannot be effectively
assessed in the test environment.
Note:
On Windows Server 2003, removing the debug programs right may result in an inability to use
the Windows Update service. However, patches can still be manually downloaded and installed or
applied through other means.
Deny access to this computer from the network
Member Server Default
Legacy Client
Enterprise Client
High Security Client
SUPPORT_388945a0 ANONOYMOUS
LOGON; Built-in
Administrator, Guests;
Support_388945a0;
Guest; all
NONOperating System
service accounts
ANONOYMOUS
LOGON; Built-in
Administrator, Guests;
Support_388945a0;
Guest; all
NONOperating System
service accounts
ANONOYMOUS
LOGON; Built-in
Administrator, Guests;
Support_388945a0;
Guest; all
NONOperating System
service accounts
Important:
For all HP NAS server systems, administrators should only deny the Support_388945a0
account.
Note:
ANONOYMOUS LOGON, Built-in Administrator, Support_388945a0; Guest; and all NON-
operating system service accounts are not included in the .inf security template. These accounts and
groups have unique SIDs for each domain in the network. Therefore, they must be added manually.
For further information, see the Manual Hardening Procedures in section 2.8.7.
The
Deny access to this computer from the network
user right determines which users are prevented
from accessing a computer over the network. This user right will deny a number of network protocols
including SMB-based protocols, NetBIOS, CIFS, HTTP. and COM+. This policy setting supersedes the
Access this computer from the network
user right when a user account is subject to both policies.
Configuring this logon right for other groups could limit the abilities of users assigned to specific
administrative roles within the network. Verify that delegated tasks will not be negatively impacted.
















































