94
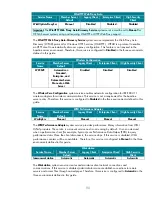
Subkey Registry Value Entry
Format
Recommended Value (Decimal)
EnableICMPRedirect DWORD
0
SynAttackProtect DWORD
1
EnableDeadGWDetect DWORD
0
EnablePMTUDiscovery DWORD
0
KeepAliveTime DWORD
300,000
DisableIPSourceRouting DWORD
2
TcpMaxConnectResponseRetransmissions DWORD
2
TcpMaxDataRetransmissions DWORD
3
PerformRouterDiscovery DWORD
0
TCPMaxPortsExhausted DWORD
5
EnableICMPRedirect: Allow ICMP redirects to override OSPF generated
routes
This entry appears as
MSS: Allow ICMP redirects to override OSPF generated routes
in the SCE.
Internet Control Message Protocol (ICMP) redirects cause the stack to plumb host routes. These routes
override the Open Shortest Path First (OSPF)-generated routes.
Vulnerability:
This behavior is expected; the problem is that the 10 minute time-out period for the
ICMP redirect-plumbed routes temporarily creates a black hole for the network where traffic will no
longer be routed properly for the affected host.
Countermeasure
:
Configure
MSS: Allow ICMP redirects to override OSPF generated routes
to a
value of
Disabled
. The possible values for this Registry value are:
•
1
or
0
; default is
1
(enabled)
In the SCE UI, these options appear as:
•
Enabled
•
Disabled
•
Not Defined
Potential
Impact:
When Routing and Remote Access Service (RRAS) is configured as an
autonomous system boundary router (ASBR), it does not correctly import connected interface subnet
routes. Instead, this router injects host routes into the OSPF routes. Because the OSPF router can not
be used as an ASBR router, importing connected interface subnet routes into OSPF results in confusing
routing tables with strange routing paths.
SynAttackProtect: Syn attack protection level (protects against DoS
This entry appears as
MSS: Syn attack protection level (protects against DoS)
in the SCE. This registry
value causes TCP to adjust retransmission of SYN-ACKs. When administrators configure this value, the
connection responses time-out more quickly in the event of a connect request (SYN) attack.
Vulnerability:
In a SYN flood attack, the attacker sends a continuous stream of SYN packets to a
server, and the server leaves the half-open connections open until it is overwhelmed and is no longer
able to respond to legitimate requests