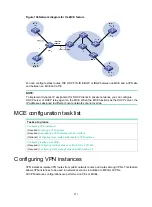
513
Step Command
Remarks
2.
Enter VPN instance
view or IPv4 VPN view
•
Enter VPN instance view:
ip vpn-instance
vpn-instance-name
•
Enter IPv4 VPN view:
a. ip vpn-instance
vpn-instance-name
b. address-family ipv4
Configurations made in VPN
instance view apply to both IPv4
VPN and IPv6 VPN.
IPv4 VPN prefers the
configurations in IPv4 VPN view
over the configurations in VPN
instance view.
3.
Configure route targets.
vpn-target
vpn-target
&<1-8> [
both
|
export-extcommunity
|
import-extcommunity
]
By default, no route targets are
configured.
4.
Set the maximum
number of active routes.
routing-table
limit
number
{
warn-threshold
|
simply-alert
}
By default, the maximum number
of active routes is 500100.
Setting the maximum number of
active routes for a VPN instance
can prevent the PE from learning
too many routes.
5.
Apply an import routing
policy.
import route-policy
route-policy
By default, all routes matching the
import target attribute are
accepted.
The specified routing policy must
have been created.
For information about routing
policies, see
Layer 3—IP
Routing
Configuration Guide.
6.
Apply an export routing
policy.
export route-policy
route-policy
By default, routes to be advertised
are not filtered.
The specified routing policy must
have been created.
For information about routing
policies, see
Layer 3—IP
Routing
Configuration Guide.
7.
Apply a tunnel policy to
the VPN instance.
tnl-policy
tunnel-policy-name
By default, only one tunnel is
selected (no load balancing) in
this order: LSP tunnel, GRE
tunnel, and CR-LSP tunnel.
The specified tunnel policy must
have been created.
For information about tunnel
policies, see "Configuring tunnel
policies."
Configuring routing on an MCE
MCE implements service isolation through route isolation. MCE routing configuration includes the
following:
•
MCE-VPN site routing configuration.
•
MCE-PE routing configuration.
On the PE, perform the following tasks:
•
Disable routing loop detection to avoid route loss during route calculation.
•
Disable route redistribution between routing protocols to save system resources.