Extended ACL:
Use extended ACLs for a port or trunk if you need the following:
•
Source and destination IP addresses
•
TCP application criteria
•
UDP application criteria
Concurrent IPv4 and IPv6 ACLs
You can implement concurrent configuration and concurrent configuration and operation of IPv4
and IPv6 ACLs. For information on IPv4 ACL, see the latest HP Switch Software Access Security
Guide for your switch
ACL inbound application points
You can apply ACL filtering to IP traffic inbound on a physical port or static trunk with a destination
(DA):
•
On another device. (ACLs are not supported on dynamic LACP trunks.)
•
On the switch itself. In
“Example of filter applications” (page 59)
, this would be any of the IP
addresses shown in VLANs "A", "B", and "C" on the switch. (IP routing need not be enabled.)
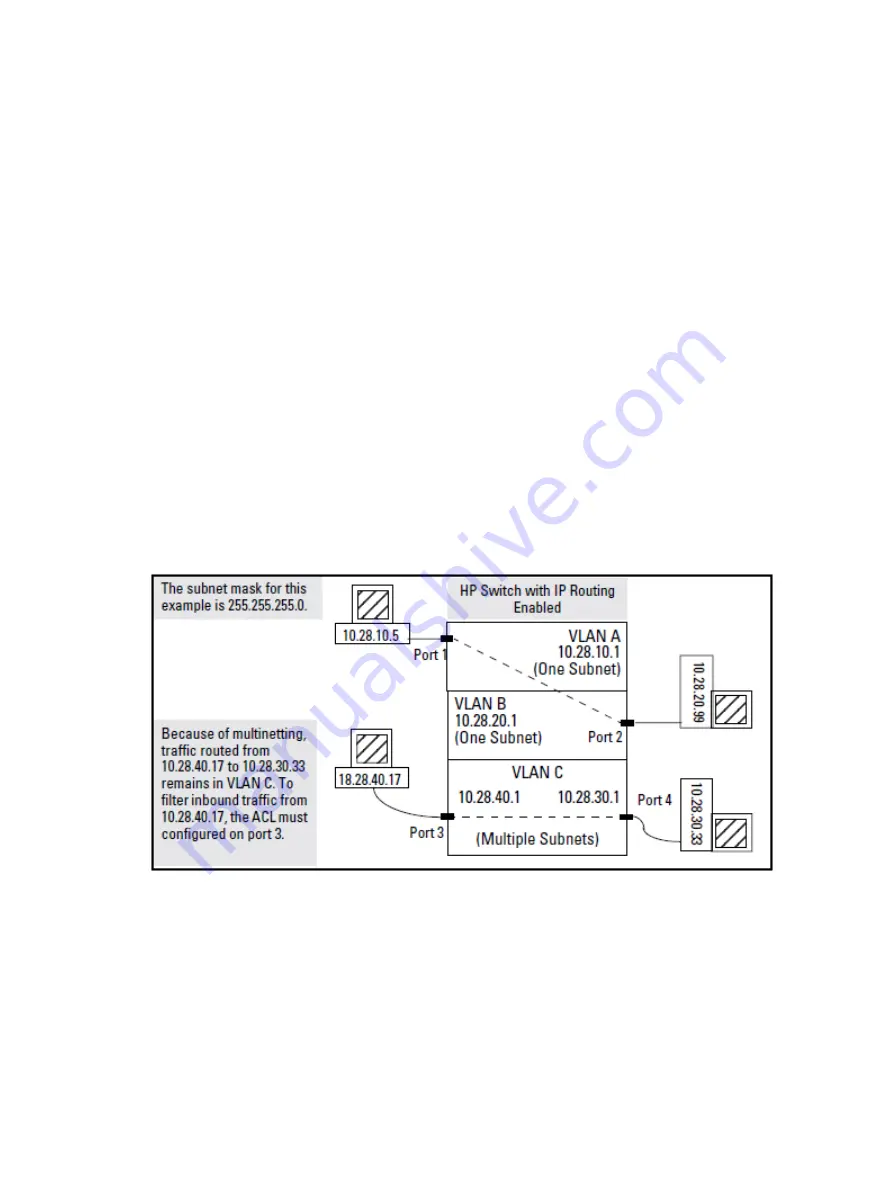
The switch can apply ACL filtering to traffic entering the switch on ports or trunks configured to
apply ACL filters. For example, in
“Example of filter applications” (page 59)
assign an inbound
ACL on port 1 to filter a packet from the workstation 10.28.10.5 to the server at 10.28.20.99.
All ACL filtering is performed on the inbound port or trunk. Routing may be enabled or disabled
on the switch, and any permitted inbound traffic may have any valid destination.
Figure 16 Example of filter applications
VACL applications
IPv6 VACLs filter traffic entering the switch on a VLAN configured with the "VLAN" ACL option.
vlan <vid> ipv6 access-group <vacl-identifier> vlan
As shown in
“Example of VACL filter applications on IPv6 traffic entering the switch” (page 60)
assign a VACL to VLAN 2 to filter all inbound switched or routed IPv6 traffic received from clients
on the 2001:db8:0:222:: network. Routed IPv6 traffic received on VLAN 2 from VLANs 1 or 3 is
not filtered by the VACL on VLAN 2.
IPv6 ACLs
59
















































