To view the access control list, navigate to
Active Directory Users and Computers
, open the
Properties
page for the role object, and then click the
Security
tab. The Advanced View must be enabled
in MMC to view the
Security
tab.
Role-based time restrictions
Administrators can place time restrictions on LOM roles. Users are granted the rights specified for the
LOM devices listed in the role only if they are members of the role and meet the time restrictions for the
role.
Role-based time restrictions can be met only if the time is set on the LOM device. LOM devices use local
host time to enforce time restrictions. If the LOM device clock is not set, the role-based time restriction
fails unless no time restrictions are specified for the role. The time is normally set when the host is
booted.
The time setting can be maintained by configuring SNTP, which allows the LOM device to compensate for
leap years and minimize clock drift with respect to the host. Events, such as unexpected power loss or
flashing LOM firmware, can cause the LOM device clock not to be set. The host time must be correct for
the LOM device to preserve the time setting across firmware flashes.
Role-based address restrictions
The LOM firmware enforces role-based address restrictions based on the client IP network address.
When the address restrictions are met for a role, the rights granted by the role apply.
Address restrictions can be difficult to manage when access is attempted across firewalls or through
network proxies. Either of these mechanisms can change the apparent network address of the client,
causing the address restrictions to be enforced in an unexpected manner.
Multiple restrictions and roles
The most useful application of multiple roles is restricting one or more roles so that rights do not apply in
all situations. Other roles provide different rights under different constraints. Using multiple restrictions
and roles enables the administrator to create arbitrary, complex rights relationships with a minimum
number of roles.
For example, an organization might have a security policy in which LOM administrators are allowed to use
the LOM device from within the corporate network, but can reset the server only after regular business
hours.
Directory administrators might be tempted to create two roles to address this situation, but extra caution is
required. Creating a role that provides the required server reset rights and restricting it to after hours
might allow administrators outside the corporate network to reset the server, which is contrary to most
security policies.
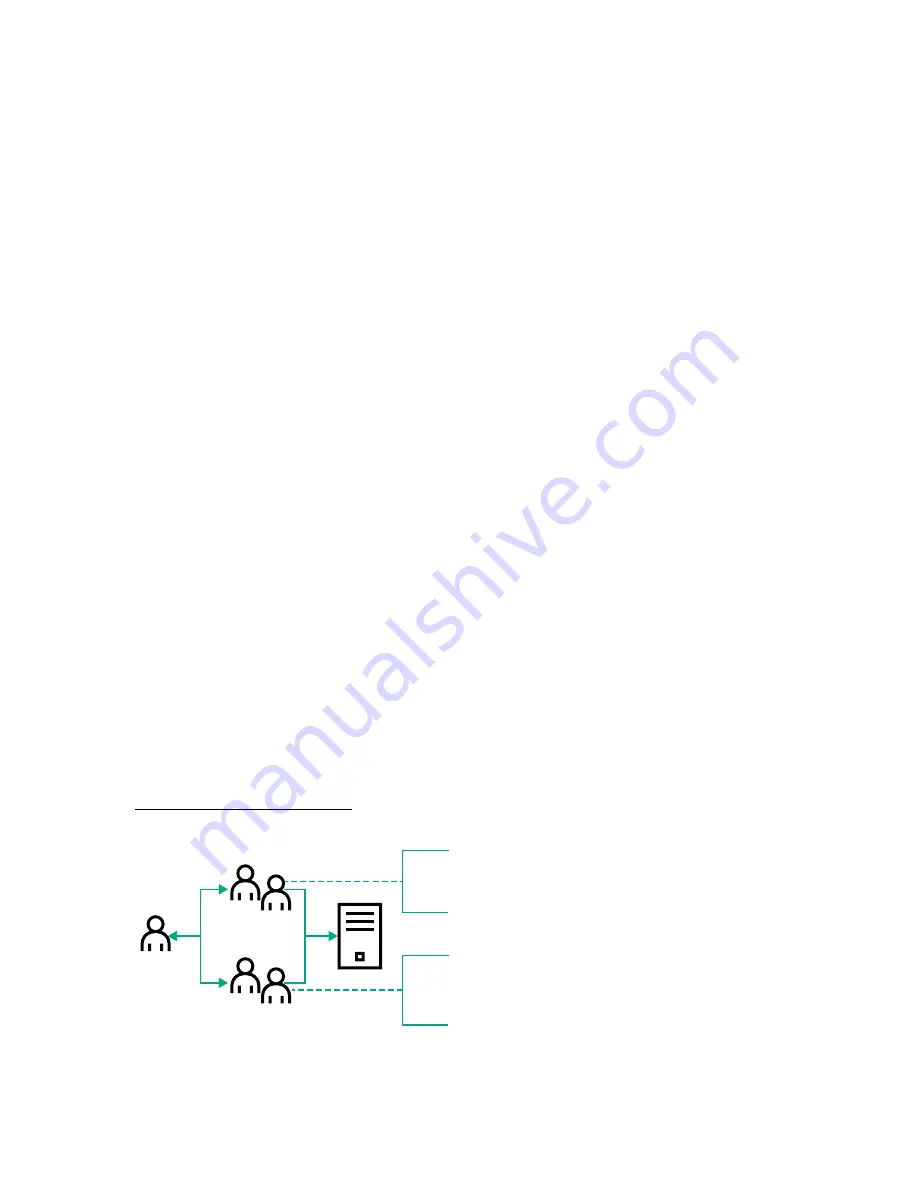
Creating restrictions and roles
shows a security policy that dictates that general use is restricted to
clients in the corporate subnet, and server reset capability is restricted to after hours.
User
General Use
role
Reset role
Assigns Login privilege
IP Restrictions:
DENY
except to corporate subnet
Server
Assigns Virtual Power and
Reset privilege
Time Restriction: Denied Monday
through Friday, 8 a.m. to 5 p.m.
Figure 12: Creating restrictions and roles
Role-based time restrictions
331