498
Verifying the configuration
•
After the configuration, an SNMP connection is established between the NMS and the agent. The
NMS can get and configure the values of some parameters on the agent through MIB nodes.
•
Disable or enable an idle interface on the device, and the NMS receives the corresponding trap.
SNMPv3 configuration example
Network requirements
As shown in
, the NMS (1.1.1.2/24) uses SNMPv3 to monitor and manage the interface status
of the agent (1.1.1.1/24), and the agent automatically sends traps to report events to the NMS.
The NMS and the agent perform authentication when they set up an SNMP session. The authentication
algorithm is MD5 and the authentication key is
authkey
. The NMS and the agent also encrypt the SNMP
packets between them by using the DES algorithm and the privacy key
prikey
.
Figure 524
Network diagram
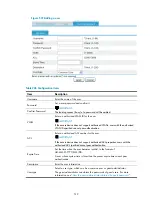
Configuring the SNMP agent
1.
Select
System Management
>
SNMP
from the navigation tree, and then perform the following
configurations, as shown in
.
Figure 525
Configuring the SNMP agent
2.
Select the
Enable
radio box.
3.
Select the
SNMPv3
radio box.
4.
Type
user1
in the field of
Security Username
.
5.
Type
authkey
in the field of
Authentication Password
.
Summary of Contents for MSR SERIES
Page 17: ...xv Documents 835 Websites 835 Conventions 836 Index 838 ...
Page 20: ...3 Figure 3 Initial page of the Web interface ...
Page 42: ...25 Figure 13 Firefox Web browser setting ...
Page 59: ...42 Figure 27 Checking the basic service configuration ...
Page 73: ...56 Figure 35 Sample interface statistics ...
Page 156: ...139 Figure 139 Rebooting the 3G modem ...
Page 168: ...151 Figure 152 Configuring Web server 2 ...
Page 174: ...157 Figure 158 Configure the URL filtering function ...
Page 242: ...225 Figure 233 Enabling the DHCP client on interface Ethernet 0 1 ...
Page 247: ...230 Figure 236 The page for configuring an advanced IPv4 ACL ...
Page 255: ...238 Figure 241 Advanced limit setting ...
Page 298: ...281 e Click Apply 2 Configure Router B in the same way Router A is configured ...
Page 400: ...383 Figure 387 Verifying the configuration ...
Page 405: ...388 ...
Page 523: ...506 Figure 530 Ping configuration page ...
Page 775: ...758 Figure 785 Configuring a jump node ...