777
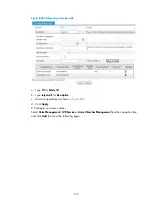
a.
Type
30000
for
Number ID
.
b.
Type
300
for
Number
.
c.
Select
call500
from the
Bind to Menu
list.
d.
Click
Apply
.
For other settings, see
Verifying the configuration
Dial 300 at Telephone A. Telephone B rings.
Configure a secondary call on a service node
Network requirements
As shown in
, configure an IVR access number and service node functions on Router B to meet
the following requirements.
•
After the subscriber dials
300
(the IVR access number) from Telephone A, Router B plays the audio
file
bye.wav
, and then terminates the call.
•
If the subscriber dials a wrong number at Telephone A, Router B plays the audio file
input_error.wav
.
•
If no number is dialed at Telephone A within the timeout time, Router B plays the audio file
timeout.wav
.
Figure 805
Network diagram
Configuration procedure
1.
Configure Router A: See
2.
Configure Router B:
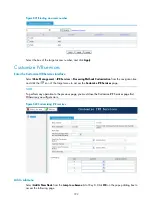
# Configure a service node.
Select
Voice Management
>
IVR Services
>
Advanced Settings
from the navigation tree, select the
Configure Service Node
tab, and click
Add
to access the following page.
Summary of Contents for MSR SERIES
Page 17: ...xv Documents 835 Websites 835 Conventions 836 Index 838 ...
Page 20: ...3 Figure 3 Initial page of the Web interface ...
Page 42: ...25 Figure 13 Firefox Web browser setting ...
Page 59: ...42 Figure 27 Checking the basic service configuration ...
Page 73: ...56 Figure 35 Sample interface statistics ...
Page 156: ...139 Figure 139 Rebooting the 3G modem ...
Page 168: ...151 Figure 152 Configuring Web server 2 ...
Page 174: ...157 Figure 158 Configure the URL filtering function ...
Page 242: ...225 Figure 233 Enabling the DHCP client on interface Ethernet 0 1 ...
Page 247: ...230 Figure 236 The page for configuring an advanced IPv4 ACL ...
Page 255: ...238 Figure 241 Advanced limit setting ...
Page 298: ...281 e Click Apply 2 Configure Router B in the same way Router A is configured ...
Page 400: ...383 Figure 387 Verifying the configuration ...
Page 405: ...388 ...
Page 523: ...506 Figure 530 Ping configuration page ...
Page 775: ...758 Figure 785 Configuring a jump node ...