701
Figure 723
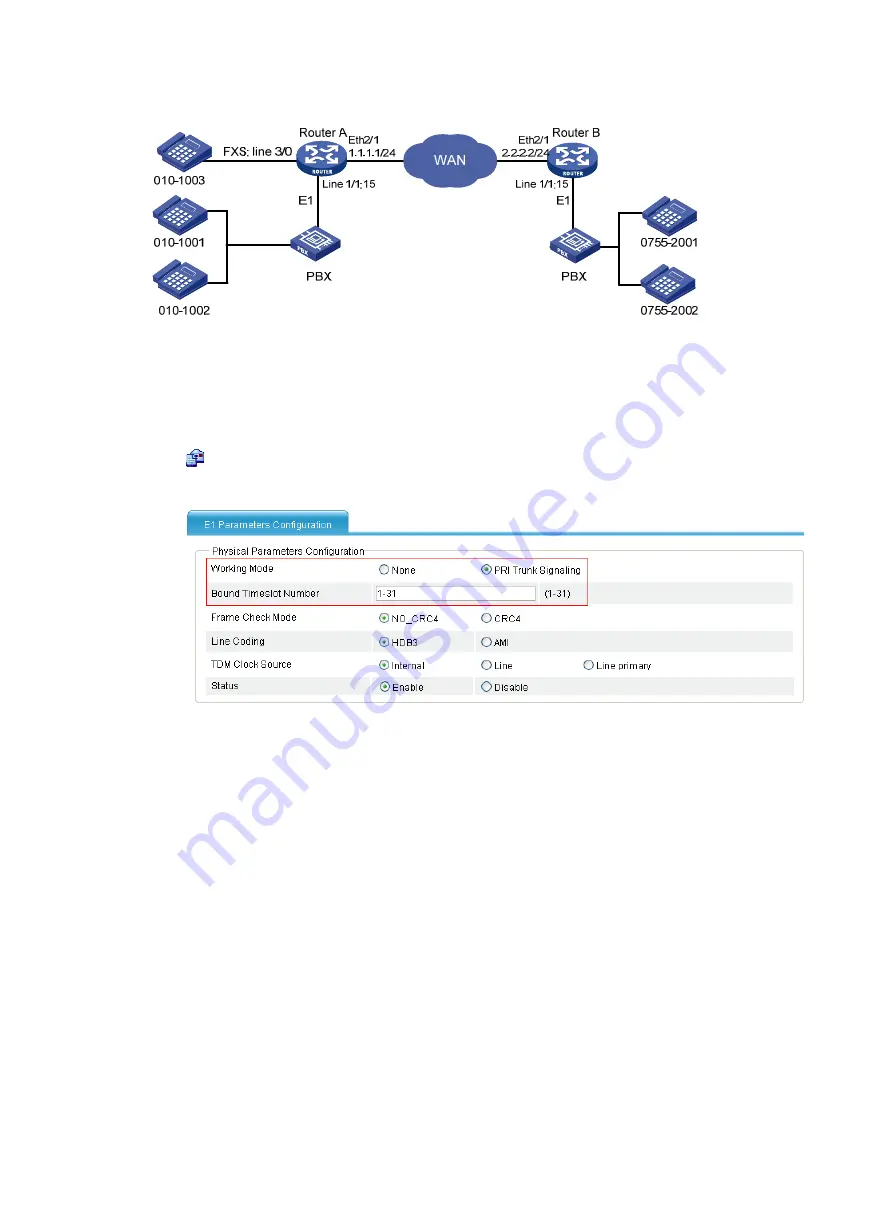
Network diagram
Configuration procedure
1.
Configure Router A:
# Configure an ISDN PRI group.
Select
Voice Management
>
Digital Link Management
from the navigation tree, and then click the
icon of
E1 1/1
to access the E1 parameters configuration page.
Figure 724
E1 parameters configuration page
a.
Select the
PRI Trunk Signaling
option. For other options, use the default settings.
b.
Click
Apply
.
# Configure local numbers and call routes.
c.
Configure a local number in the local number configuration page: The number ID is 1003, the
number is 0101003, and the bound line is 3/0.
d.
Configure a call route in the call route configuration page: The call route ID is 1001, the
destination number is 0101001, and the trunk route line is 1/1:15. In addition, to select the
Send All Digits of a Called Number
option in the
Called Number Sending Mode
area when you
configure the advanced settings of this call route.
e.
Configure a call route in the call route configuration page: The call route ID is 1002, the
destination number is 0101002, and the trunk route line is 1/1:15. In addition, select the
Send All Digits of a Called Number
option in the
Called Number Sending Mode
area when you
configure the advanced settings of this call route.
f.
Configure a call route in the call route configuration page: The call route ID is 0755, the
destination number is 0755...., and the call route type is SIP, the SIP routing type is IP routing,
and the destination address is 2.2.2.2.
2.
Configure Router B.
Summary of Contents for MSR SERIES
Page 17: ...xv Documents 835 Websites 835 Conventions 836 Index 838 ...
Page 20: ...3 Figure 3 Initial page of the Web interface ...
Page 42: ...25 Figure 13 Firefox Web browser setting ...
Page 59: ...42 Figure 27 Checking the basic service configuration ...
Page 73: ...56 Figure 35 Sample interface statistics ...
Page 156: ...139 Figure 139 Rebooting the 3G modem ...
Page 168: ...151 Figure 152 Configuring Web server 2 ...
Page 174: ...157 Figure 158 Configure the URL filtering function ...
Page 242: ...225 Figure 233 Enabling the DHCP client on interface Ethernet 0 1 ...
Page 247: ...230 Figure 236 The page for configuring an advanced IPv4 ACL ...
Page 255: ...238 Figure 241 Advanced limit setting ...
Page 298: ...281 e Click Apply 2 Configure Router B in the same way Router A is configured ...
Page 400: ...383 Figure 387 Verifying the configuration ...
Page 405: ...388 ...
Page 523: ...506 Figure 530 Ping configuration page ...
Page 775: ...758 Figure 785 Configuring a jump node ...