Folder, Printer, and Share Management
141
NAS 4000s and 9000s Administration Guide
Protocol Parameter Settings
As previously mentioned, the NAS server supports the following protocols:
■
DFS
■
NFS
■
FTP
■
HTTP
■
Microsoft SMB
This section discusses the parameter settings for each protocol type.
Note:
See the protocol section of the Cluster Administration chapter for information about protocol
selection and management in a cluster.
To access and enter protocol parameter settings:
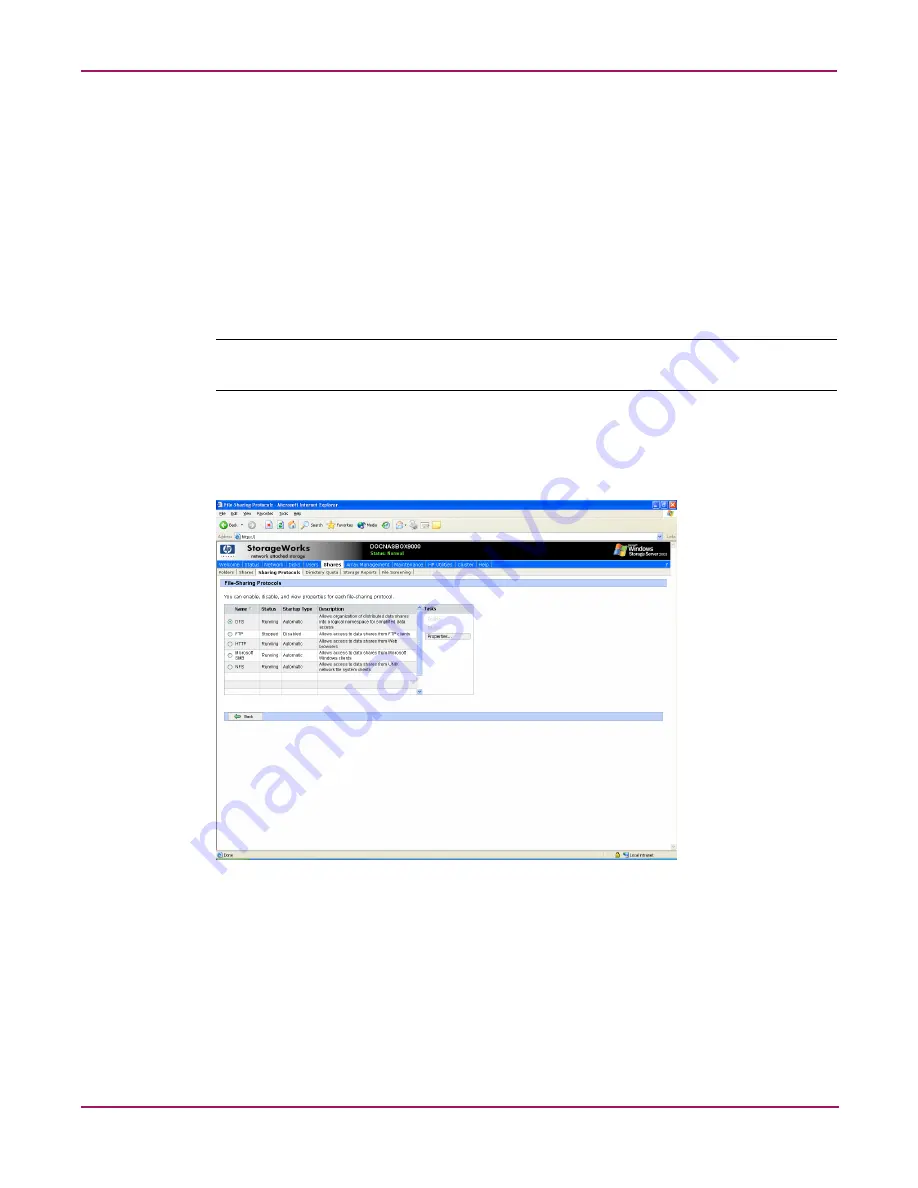
1. From the Shares menu, select Sharing Protocols. The File-Sharing Protocols dialog box
is displayed.
Figure 80: File-Sharing Protocols dialog box
2. Protocols and their statuses are listed. The following options are available:
■
Enabling a protocol
■
Disabling a protocol
■
Modifying Protocol Settings
Because enabling and disabling a protocol are self explanatory, only modifying protocol
specific settings is described in this section.
Summary of Contents for NAS 4000s
Page 18: ...About this Guide 18 NAS 4000s and 9000s Administration Guide ...
Page 92: ...Disk Management 92 NAS 4000s and 9000s Administration Guide ...
Page 196: ...NetWare File System Management 196 NAS 4000s and 9000s Administration Guide ...
Page 246: ...Index 246 NAS 4000s and 9000s Administration Guide ...
















































