Basic Administrative Procedures and Setup Completion
39
NAS 4000s and 9000s Administration Guide
Installing the HP Network Teaming Utility
Before using the HP Network Teaming utility, it must be installed.
Note:
Installing and configuring NIC teaming should always be performed via iLO port or the
console using a direct attached keyboard, monitor, and mouse since IP connections could be reset
during the configuration process. Do not use Remote Desktop.
To install the HP Network Teaming utility:
1. In the URL field of the Web browser, enter the IP address of the Integrated Lights-Out
port.
Note:
The iLO port requires a license key. The key is included with the product inside the Country
Kit. Refer to the iLO Advanced License Pack for activation instructions.
Note:
The iLO port can also be accessed from the HP Utilities tab of the WebUI by clicking the
remote management link.
2. At the Integrated Lights-Out Account Login screen, supply the username and password for
the iLO and click Login.
3. Click the Remote Console tab. The Remote Console Information screen is displayed.
4. Click on the Remote Console choice in the menu on the left side of the screen.
5. Press the Ctrl-Alt-Del button to login to the console.
6. Supply an administrator username and password. The NAS server desktop is displayed.
7. Double-click the NIC Team Setup icon on the desktop.
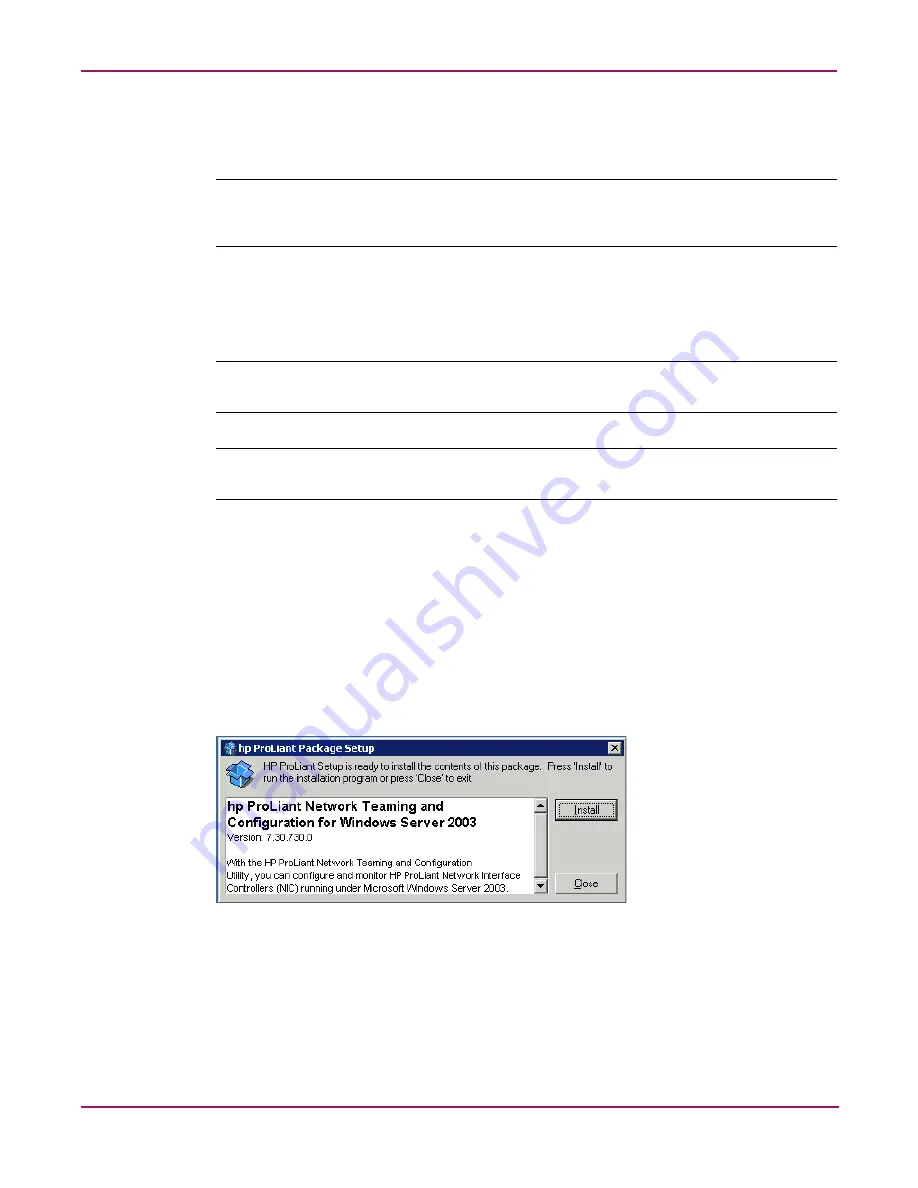
8. When the following message box is displayed, click Install.
Figure 13: Installing Network Teaming
9. When the installation process is complete, the following screen is displayed. Click Close.
Summary of Contents for NAS 4000s
Page 18: ...About this Guide 18 NAS 4000s and 9000s Administration Guide ...
Page 92: ...Disk Management 92 NAS 4000s and 9000s Administration Guide ...
Page 196: ...NetWare File System Management 196 NAS 4000s and 9000s Administration Guide ...
Page 246: ...Index 246 NAS 4000s and 9000s Administration Guide ...
















































