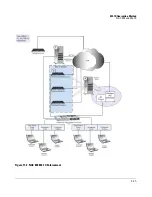
802.1X Quarantine Method
Setting up the 802.1X Components
11-19
h.
Open the
Certificates
folder under the
Console Root
.
i.
Right-click on the
Personal
folder and select
All Tasks>>Request New
Certificate
.
NOTE:
To import the certificate manually:
1. Right-click on the Personal folder>>select All Tasks>>Import.
2. When the wizard opens, click Next.
3.Enter the path to the NAC 800 certificate, for example:
D:\support\ias\compliance.keystore.cer
4.Click Next, Next, and Finish.
j.
Follow the instructions to generate a certificate request. If there are
no certificate templates available you need to edit the certificate
template permissions (in
mmc
add the certificate template snap-in,
right-click on the template, select
properties
, and change the
permissions for your user) on the certificate authority. The Computer
or RAS and IAS templates both work.
k.
Once the Certificate is granted by the certificate authority, return to
the IAS policy editor to continue the setup.
l.
Click
Configure
to configure the certificate for use with the PEAP
authentication method. The Protected EAP Properties window
appears (figure 11-18).
m. Select the certificate you created in the previous steps, select the EAP
types you want to use, and click
OK
.
n.
Once the Certificate is granted by the certificate authority, edit the
IAS policy.
o.
On the
authentication
tab click
authentication methods
.
p.
Select
PEAP
and click
Edit
.
q.
Select the new certificate and click
Apply
.
Summary of Contents for ProCurve NAC 800
Page 1: ...HP ProCurve Network Access Controller 800 Users Guide ...
Page 2: ......
Page 3: ...ProCurve Network Access Controller 800 Release 1 1 Users Guide ...
Page 43: ...2 1 2 Clusters and Servers Chapter Contents Overview 2 2 Installation Examples 2 3 ...
Page 71: ...System Configuration Management Server 3 23 Figure 3 9 System Configuration Management Server ...
Page 80: ...System Configuration User Accounts 3 32 Figure 3 12 System Configuration User Accounts ...
Page 88: ...System Configuration User Roles 3 40 Figure 3 16 System Configuration User Roles ...
Page 180: ... This page intentionally left blank ...
Page 208: ... This page intentionally left blank ...
Page 234: ...End user Access Mac OS X Endpoint Settings 5 26 Figure 5 14 Mac System Preferences ...
Page 288: ... This page intentionally left blank ...
Page 302: ... This page intentionally left blank ...
Page 306: ...High Availability and Load Balancing High Availability 8 4 Figure 8 2 DHCP Installation ...
Page 307: ...High Availability and Load Balancing High Availability 8 5 Figure 8 3 802 1X Installation ...
Page 309: ...9 1 9 Inline Quarantine Method Chapter Contents Inline 9 2 ...
Page 312: ... This page intentionally left blank ...
Page 315: ...DHCP Quarantine Method Overview 10 3 Figure 10 1 DHCP Installation ...
Page 318: ... This page intentionally left blank ...
Page 323: ...802 1X Quarantine Method NAC 800 and 802 1X 11 5 Figure 11 2 NAC 800 802 1X Enforcement ...
Page 324: ...802 1X Quarantine Method NAC 800 and 802 1X 11 6 Figure 11 3 802 1X Communications ...
Page 380: ... This page intentionally left blank ...
Page 418: ... This page intentionally left blank ...
Page 425: ...Reports Viewing Report Details 14 7 Figure 14 3 Test Details Report ...
Page 459: ...System Administration Creating and Replacing SSL Certificates 15 31 10 Save and exit the file ...
Page 468: ... This page intentionally left blank ...
Page 480: ... This page intentionally left blank ...
Page 526: ...Tests Help Security Settings Windows B 34 http www pcworld com article id 112138 article html ...
Page 532: ... This page intentionally left blank ...
Page 562: ... This page intentionally left blank ...