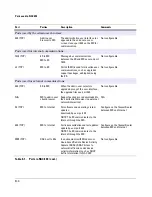
Ports used in NAC 800
E-2
Ports used by the admin user browser:
443 (TCP)
Admin user
browser to MS
The administration user interface (as
opposed to the end user access
screens) uses port 443 on the MS for
communication.
Not configurable
Ports used for internal communications:
7483 (TCP)
ES to MS
MS to ES
Message bus communications
between the ES and MS occur on port
7483.
Not configurable
22 (TCP)
MS to ES
Port 22 (SSH) is used for miscellaneous
communications, such as upgrades,
support packages, adding/removing
the ES.
Not configurable
Ports used for external communications:
443 (TCP)
ES to MS
When the admin user selects to
upgrade by way of the user interface,
the upgrade files use port 443.
Not configurable
N/A
MS to admin user
client browser
Support packages are downloaded to
the admin client browser (no external
network interaction)
N/A
80 (TCP)
MS to Internet
For software and operating system
updates:
download.hp.com port 80
NOTE: The ES communicates to the
Internet through the MS.
Configure on the firewall/router
between MS and Internet
443 (TCP)
MS to Internet
For license validation and test updates:
update.hp.com port 443
NOTE: The ES communicates to the
Internet through the MS.
Configure on the firewall/router
between MS and Internet
8999 (TCP)
DAC host to ESs
In environments with Windows- or
Linux-based Remote Device Activity
Capture (RDAC), RDAC listens to
network traffic and sends device
activity information (such as DHCP
traffic information) to NAC 800."
Not configurable
Port
Parties
Description
Comments
Table E-1.
Ports in NAC 800 (cont.)
Summary of Contents for ProCurve NAC 800
Page 1: ...HP ProCurve Network Access Controller 800 Users Guide ...
Page 2: ......
Page 3: ...ProCurve Network Access Controller 800 Release 1 1 Users Guide ...
Page 43: ...2 1 2 Clusters and Servers Chapter Contents Overview 2 2 Installation Examples 2 3 ...
Page 71: ...System Configuration Management Server 3 23 Figure 3 9 System Configuration Management Server ...
Page 80: ...System Configuration User Accounts 3 32 Figure 3 12 System Configuration User Accounts ...
Page 88: ...System Configuration User Roles 3 40 Figure 3 16 System Configuration User Roles ...
Page 180: ... This page intentionally left blank ...
Page 208: ... This page intentionally left blank ...
Page 234: ...End user Access Mac OS X Endpoint Settings 5 26 Figure 5 14 Mac System Preferences ...
Page 288: ... This page intentionally left blank ...
Page 302: ... This page intentionally left blank ...
Page 306: ...High Availability and Load Balancing High Availability 8 4 Figure 8 2 DHCP Installation ...
Page 307: ...High Availability and Load Balancing High Availability 8 5 Figure 8 3 802 1X Installation ...
Page 309: ...9 1 9 Inline Quarantine Method Chapter Contents Inline 9 2 ...
Page 312: ... This page intentionally left blank ...
Page 315: ...DHCP Quarantine Method Overview 10 3 Figure 10 1 DHCP Installation ...
Page 318: ... This page intentionally left blank ...
Page 323: ...802 1X Quarantine Method NAC 800 and 802 1X 11 5 Figure 11 2 NAC 800 802 1X Enforcement ...
Page 324: ...802 1X Quarantine Method NAC 800 and 802 1X 11 6 Figure 11 3 802 1X Communications ...
Page 380: ... This page intentionally left blank ...
Page 418: ... This page intentionally left blank ...
Page 425: ...Reports Viewing Report Details 14 7 Figure 14 3 Test Details Report ...
Page 459: ...System Administration Creating and Replacing SSL Certificates 15 31 10 Save and exit the file ...
Page 468: ... This page intentionally left blank ...
Page 480: ... This page intentionally left blank ...
Page 526: ...Tests Help Security Settings Windows B 34 http www pcworld com article id 112138 article html ...
Page 532: ... This page intentionally left blank ...
Page 562: ... This page intentionally left blank ...